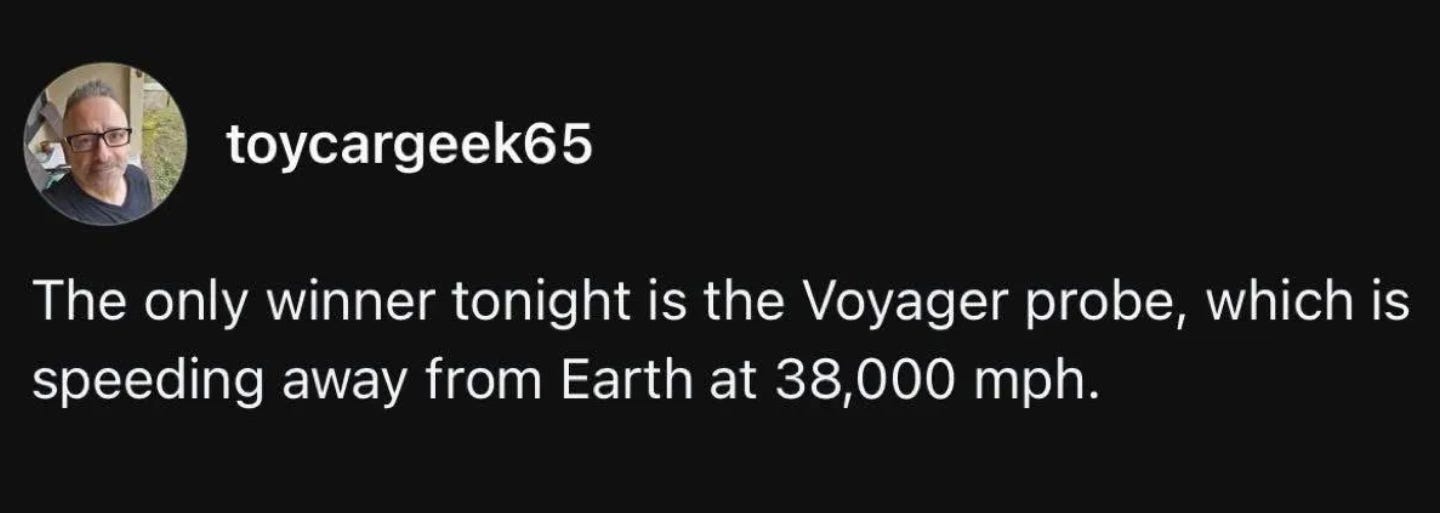
Tuesday 2026-03-10
09:00 AM
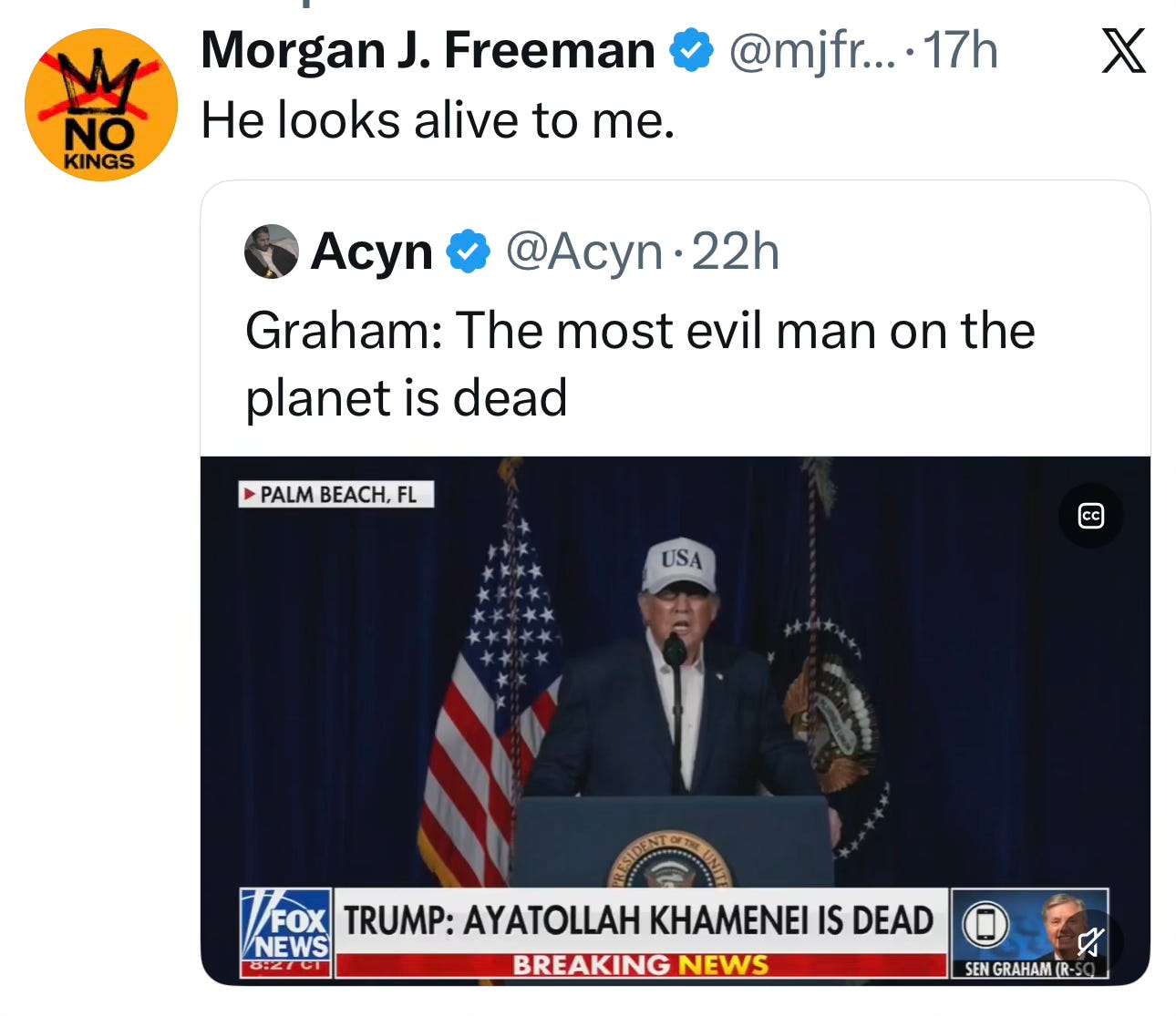
DOJ Un-Drops Its Appeal Against Law Firms, Files Brief That Gets The First Amendment Exactly Backwards [Techdirt]
On Wednesday of last week, I wrote a post about how the Trump administration had quietly given up defending its unconstitutional executive orders targeting law firms. The DOJ was dropping its appeals, the firms that fought had won, and the firms that capitulated—led by Paul Weiss and their nearly $1 billion in groveling pro bono commitments—were left holding a very expensive bag.
What I did not realize, because this administration launches new absurdities faster than any human being can reasonably track them, was that the day before I published that piece (but about the time I was writing it), the DOJ had already filed a motion to take back its voluntary dismissal. And then, by Friday, the DOJ had filed a full appellate brief seeking to overturn all four district court rulings that struck down the executive orders.
So, to recap the timeline here: On Monday, the DOJ told the DC Circuit it was voluntarily dropping its appeals. All four law firms agreed. Done deal. On Tuesday, the DOJ filed a motion to withdraw its own voluntary dismissal. On Wednesday, I published an article mocking the administration for giving up. On Friday, the DOJ filed a 97-page opening brief arguing that the executive orders were “well within the Presidential prerogative.”
My only defense for coming in a day late is that covering this administration in anything close to real time is effectively impossible.
Let’s start with the procedural absurdity before we get to the substance—because the procedural absurdity is really something.
The motion to withdraw the voluntary dismissal is a remarkable document, mostly for how little it says. The entire operative section is barely over a hundred words. After all parties had agreed to the dismissal, the DOJ simply asked to take it back, offering no explanation whatsoever. The law firms’ collective response, included in the filing itself, was about as polite as you’d expect:
“Plaintiffs-Appellees oppose the government’s unexplained request to withdraw yesterday’s voluntary dismissal, to which all parties had agreed. Under no circumstances should the government’s unexplained about-face provide a basis for an extension of its brief.”
“Unexplained.” That word does a lot of heavy lifting. The DOJ’s motion doesn’t even try to explain why it changed course. There’s no “upon further reflection” or “new developments have arisen.” Just: forget what we agreed to yesterday, the court hasn’t formally granted the dismissal yet, so we’d like to un-dismiss please.
As of this writing, the court hasn’t ruled on that motion. But the DOJ apparently decided not to wait around and went ahead and filed its full appellate brief on Friday anyway.
The opening paragraph of the DOJ’s appellate brief is genuinely one of the more audacious things I’ve read in a legal filing, and I say that as someone who reads a lot of legal filings:
Courts cannot tell the President what to say. Courts cannot tell the President what not to say. They cannot tell the President how to handle national security clearances. And they cannot interfere with Presidential directives instructing agencies to investigate racial discrimination that violates federal civil rights laws.
Let’s focus on those first two sentences, because they reveal something important about how the administration is framing this case—and how badly they’re getting the First Amendment backwards.
“Courts cannot tell the President what to say. Courts cannot tell the President what not to say.”
Well, sure. In the most general sense, that’s true. The president can stand at a podium and say whatever he wants. He can say mean things about law firms. He can call them names on social media. He can go on television and express his displeasure with their client choices. That’s all government speech, and it’s all fine.
But that’s… not what happened here. What happened here is that the president issued executive orders imposing concrete sanctions on specific law firms—revoking security clearances, directing the termination of government contracts, restricting access to federal buildings, banning the hiring of their employees—because those firms represented clients the president didn’t like and employed lawyers who had been involved in investigations the president found personally disagreeable.
The brief tries to frame the courts’ injunctions as an attempt to “silence” the president. But nobody is trying to silence the president. The president can talk about these law firms every day from now until the world ends. What the courts said—four separate times—is that the president cannot use the machinery of government to punish law firms for their constitutionally protected legal advocacy. There’s a rather fundamental difference between speech and sanctions, and pretending not to understand that difference is doing a lot of work in this brief.
This gets at something we talk about regularly here at Techdirt: the First Amendment is a restraint on government power. It prevents the government from using its authority to suppress or punish private speech. When the DOJ frames this as courts trying to control the president’s speech, they’ve got the vector of the First Amendment claim pointing in exactly the wrong direction. The law firms aren’t saying the president can’t talk. They’re saying the president can’t retaliate against them for their own protected speech and advocacy. Those are two wildly different things.
The brief actually cites NRA v. Vullo, the 2024 Supreme Court case that we’ve written about a few times. For those unfamiliar, that case involved New York’s former superintendent of financial services, who was accused of using her regulatory power to coerce financial institutions into cutting ties with the NRA because she disagreed with the NRA’s advocacy. The Supreme Court held—unanimously—that government officials using their regulatory authority to punish or suppress disfavored private speech can violate the First Amendment, even if the official frames their actions in terms of legitimate regulatory interests.
The DOJ cites Vullo in the context of arguing that the district courts went too far in enjoining “future actions” based on Section 1 of the executive orders, quoting the district court’s ruling in favor of one of the law firms (Jenner & Block) favorably:
Significantly, even the district court in Jenner recognized this. That court declined to “enjoin future actions taken pursuant to Section 1,” because “Section 1 does not direct any action.” JA2205–06. But “shorn of its enforcement mechanisms, Section 1 is nothing more than the Executive Branch ‘saying what it wishes.’” Id. (quoting Nat’l Rifle Ass’n of Am. v. Vullo, 602 U.S. 175, 187 (2024)). “Jenner has no more right to silence the Executive Branch than the Executive Branch has to silence Jenner.” Id. That is because Section 1 is “government speech.” Id. Despite Jenner’s repeated request to enjoin Section 1 in the abstract, the district court correctly recognized that “[n]either standing doctrine nor equity generally permits such judicial prophylaxis.” JA2207. Thus, “[w]hether best viewed as a shortcoming of standing, ripeness, or” the lack of any basis in equity, “the guesswork entailed in enjoining all future uses of the sentiments expressed in Section 1 would exceed the Court’s proper role.”
The problem is that Vullo actually undercuts their entire argument. The point of the Vullo framework is that when government speech is coupled with government action designed to punish disfavored private expression, the combination can be unconstitutional coercion. The administration wants to unbundle its speech from its sanctions and defend each in isolation—”Section 1 is just government speech.” That’s precisely the move Vullo says you can’t get away with.
Meanwhile, I have to call out that the same people who argued in the Murthy v. Missouri case that any government speech criticizing private companies constituted a de facto First Amendment violation are now arguing “well, this paragraph was just speech, not retaliatory, so leave it alone.”
The brief also contains a line that should make Paul Weiss and others in the capitulation crowd feel especially great about their choices:
In recognition of those problems, many law firms agreed to address their practices and commit to providing pro bono work in the public interest.
The brief then helpfully lists them in a footnote in case anyone forgot which capitulating law firms to shun:
Allen Overy Shearman Sterling, Cadwalader, Kirkland & Ellis, Latham & Watkins, Milbank, Paul Weiss, Simpson Thacher, Skadden, and Wilkie Farr & Gallagher.
The DOJ is literally using the capitulation of those firms as evidence that the executive orders were reasonable and justified. “See? These firms agreed with us!” The firms that folded bought themselves a supporting role in the government’s brief arguing for the constitutionality of retaliating against law firms. Congratulations! Great job lawyering, guys.
Meanwhile, the four firms named in the brief who fought—Perkins Coie, Jenner & Block, WilmerHale, and Susman Godfrey—are named as parties who “instead filed suit.” See? Capitulating is the only proper move to this DOJ. Standing up for your own constitutional rights deserves punishment.
The heart of the filing is that opening framing. “Courts cannot tell the President what to say.” And the response to that is simple: nobody’s trying to. What courts can do—what they’re required to do under the First Amendment—is tell the president he cannot use executive power to punish private parties for their constitutionally protected advocacy. The fact that the DOJ appears unable or unwilling to understand this distinction tells you everything about the strength of their legal position.
As I noted last week, the administration’s decision to initially drop these appeals suggested that even a DOJ willing to argue almost anything looked at these cases and concluded it couldn’t win. The un-dropping and subsequent brief don’t change that calculus. While the DOJ offered no explanation for its reversal, the timing strongly suggests someone higher up didn’t like the press coverage of them folding and decided the political upside of continuing to threaten the legal profession outweighed the legal downside of losing again. Which, if you think about it, proves exactly what the law firms argued from the start: this was always about intimidation, never about law.
The firms that folded will keep being cited in government briefs as proof that the intimidation campaign was justified.
That’s the tax you pay for cowardice: your surrender becomes someone else’s evidence.
08:00 AM
Kanji of the Day: 机 [Kanji of the Day]
机
✍6
小6
desk, table
キ
つくえ
机上 (きじょう) — on the desk
机上の空論 (きじょうのくうろん) — armchair theory
勉強机 (べんきょうづくえ) — desk
学習机 (がくしゅうづくえ) — writing desk
長机 (ながづくえ) — long desk
事務机 (じむづくえ) — clerical desk
机下 (きか) — word of respect added to the addressee's name on a letter
机上検査 (きじょうけんさ) — desk checking
折り畳み机 (おりたたみつくえ) — folding desk
脇机 (わきづくえ) — drawer unit (next to a desk)
Generated with kanjioftheday by Douglas Perkins.
Kanji of the Day: 核 [Kanji of the Day]
核
✍10
中学
nucleus, core, kernel
カク
核兵器 (かくへいき) — nuclear weapon
核問題 (かくもんだい) — nuclear issue (esp. weapon proliferation)
核実験 (かくじっけん) — nuclear (bomb) test
核施設 (かくしせつ) — nuclear facility
中核 (ちゅうかく) — kernel
核開発 (かくかいはつ) — nuclear development
非核 (ひかく) — non-nuclear
核廃絶 (かくはいぜつ) — total abolition of nuclear weapons
核心 (かくしん) — core
核軍縮 (かくぐんしゅく) — nuclear disarmament
Generated with kanjioftheday by Douglas Perkins.
06:00 AM
Congressional Republicans Push Bills That Would Block Kids Access To Content For Ideological Reasons [Techdirt]
Should parents have a right to monitor and control which sites and apps their kids use? Today, parents do have that legal right under the Children’s Online Privacy Protection Act (COPPA). The 1998 law requires verifiable parental consent before websites or apps can collect, use or share personal information from teens 13 or under. In practice, that means parents must consent for all social media apps.
The original version of COPPA would have required parental notification whenever teens (ages 14-17) sign up for websites; parents would have had the right to access personal information shared with such sites. Those provisions were dropped after free speech advocates warned that these provisions could “chill protected First Amendment activities and undermine rather than enhance teenagers privacy,” especially when “teenagers may be divulging or seeking information they don’t want their parents to know about.” Thus, the Center for Democracy & Technology warned, while “parents have an important role in protecting their teenager’s privacy, however the bill’s emphasis on parental access may overlook older minors’ interests.”
Now, legislation is moving in Congress that would give parents the right to monitor and control the apps and platforms their teens use. Yesterday, in party-line votes, the House Energy & Commerce Committee sent two bills to the House floor. The “App Store Accountability Act” (ASAA) would require app stores to categorize users by age, associate the minors’ accounts with a parental account, and then obtain consent from the parental account when the minor user creates an account on the app store, or installs any app. This gives parents the right to monitor and control exactly which apps their kids are using. The Committee also approved the KIDS Act, which would require parental consent before any social media “platform” (website or app) could allow teens to use “any direct messaging feature.”
These bills would “make vulnerable kids less safe,” warned the committee’s Ranking Member, Frank Pallone (D-NJ), because they “threaten kids in unsupportive or even abusive households where they can be real-world harms from allowing parents complete access and control over their teens’ online existence.” This is essentially the same concern raised in 1998.
Rep. Diana Harshbarger (R-TN) was more direct than most of her Republican colleagues, insisting that parents need the bills to protect kids “who have access to these online evils.” Which evils? “Kids should not be looking at pornography—this is just common sense, people,” she said. Perhaps so: last year, the Supreme Court upheld age verification mandates for pornography in Free Speech Coalition v. Paxton (2025). But Harshbarger went much further: “We’ve been hearing from a lot of folks who profit off doing harm to kids or have questionable ideological priorities.”
Her fellow Tennessee Republican, Sen. Marsha Blackburn (R-TN), has been clear about just which “ideologies” need to be stopped. Last year, she was recorded, in remarks to a private meeting of social conservatives, saying the quiet part out loud: Republicans’ top priority should be “protecting minor children from the transgender [sic] in this culture and that influence.” Roughly half of American adults tell pollsters that trans people should be legally required to use public bathrooms that match their sex at birth, rather than the gender they identify with. Many of those parents doubtless think their teens need to be “protected” from sites and apps dedicated to helping LGBTQ teens who feel isolated and alone—apps like TrevorSpace and GiveUsTheFloor.
These sites aren’t exploiting anyone for profit. They’re both non-profits dedicated to education and building communities of the kids most at risk for mental illness and suicide. Yet ASAA and the KIDS Act would require parents to approve teens’ access to both sites. This isn’t an accident: where COPPA applies only to sites that operate “in commerce” (i.e., for profit), neither bill contains any such limit, and thus both would apply even to pure non-profits. This problem could be fixed with a surgical amendment, but Republicans would surely object and Democrats failed to raise this issue at yesterday’s markup.
Even if this problem were fixed, the larger problem would remain: for-profit apps are overwhelmingly the ones that vulnerable teens use to access perspectives on the world their parents want to block and to find other teens they can relate to. Popular apps like Snapchat and TikTok are especially vital in regions where they face hostility or violence for expressing their sexuality or gender identity. Under ASAA and the KIDS Act, parents could block such apps to “protect” their teens from “online evils” like subversive ideas about gender, sexuality, contraception or religion.
Parents could, under ASAA, also block AI apps. At a Senate hearing last year on “Examining the Harm of AI Chatbots,” one parent complained that a Character.AI chatbot had “turned [her son] against our church by convincing him that Christians are sexist and hypocritical and that God does not exist.” Sen. Josh Hawley (R-MO) told her: “You didn’t know it at the time, but the chatbot was actively indoctrinating your son into questioning your beliefs as a family, your Biblical beliefs.” Questionable “ideological priorities,” indeed.
Both bills pay lip service to the First Amendment. The KIDS Act shall not be interpreted to “[a]llow a governmental entity to enforce this Act based on a viewpoint expressed by or through any speech, expression, or information protected by the First Amendment to the Constitution of the United States.” Likewise, ASAA “shall not be construed … to affect or restrict the expression of political, religious, or other viewpoints.” These rules of construction might well help ensure that courts scrutinize selective enforcement of these bills aimed at suppressing disfavored speech. But these provisions won’t address the core problem with the bills: that parents will block viewpoints they don’t want their teens to access by controlling which apps and platforms they use.
“Constitutional rights do not mature and come into being magically only when one attains the state-defined age of majority,” as the Supreme Court has noted. “[M]inors are entitled to a significant measure of First Amendment protection,” the Court has said, “and only in relatively narrow and well-defined circumstances may government bar public dissemination of protected materials to them.”
The Court reiterated this point in Brown v. Entertainment Merchants Association (2010), which struck down age verification requirements for video games. Because virtual violence was not obscene to minors, the First Amendment applied—unlike Paxton, which upheld a Texas law requiring age verification for sites whose content was at least one third composed of pornography, which is obscene to minors. In Brown, California argued that its law was “justified in aid of parental authority: By requiring that the purchase of violent video games can be made only by adults, the Act ensures that parents can decide what games are appropriate.” The Supreme Court has long recognized “the liberty of parents and guardians to direct the upbringing and education of children under their control.” But the Brown Court doubted “that punishing third parties for conveying protected speech to children just in case their parents disapprove of that speech is a proper governmental means of aiding parental authority.” Those “doubts” should apply even more strongly to ASAA and the KIDS Act.
Rep. Harshbarger claimed that the KIDS Act hews closely to Paxton. Another member referenced the Eleventh Circuit’s recent decision in CCIA & NetChoice v. Uthmeier, which allowed a Florida law that included an age verification mandate for social media to take effect pending a First Amendment challenge. The appeals court claimed that Paxton “recently clarified that age verification does not automatically trigger strict scrutiny because it does not constitute a ‘ban on speech to adults.’”
Both misread Paxton. Here’s what the Court actually said: “the First Amendment leaves undisturbed States’ power to impose age limits on speech that is obscene to minors.” That’s irrelevant here. Like the age verification requirement for violent video games in Brown, the KIDS Act and ASAA both clearly require age verification for content that is not obscene to minors—and both bills clearly do burden the First Amendment speech of adults to access entirely lawful speech anonymously. True, ASAA tries to reduce this burden by applying the age verification mandate only to the category of users that are found likely to be minors (presumably excluding much older adults), but such a category will necessarily include many adults, who will have to identify themselves to exercise their First Amendment rights—exactly what made age verification unlawful in Brown.
TechFreedom prebutted the Eleventh Circuit’s confusion in Uthmeier. As our amicus brief explained, Paxton essentially said two things. First, for content obscene to minors, age-verification laws are (now—due to Paxton’s contortions) akin to regulations on expressive conduct. When content obscene to minors is at issue, the state’s regulatory power “necessarily includes the power to require proof of age.” In the context of adult content (pornography), in other words, an age-verification “statute can readily be understood as an effort to restrict minors’ access” to speech unprotected as to them. In the context of social media, by contrast, no such assumption applies. Restrictions in that realm remain, as they have always been, presumptively unconstitutional direct regulations on speech—as Brown held. The Eleventh Circuit simply misunderstood this, and buried its misreading of Paxton in a flimsily reasoned footnote.
So, what can lawmakers do, consistent with the First Amendment? Congress might start by creating a more privacy-protective national standard for age verification for pornography. Notably, Texas’s law does nothing to address the data security concerns raised by collecting user information for age verification.
For social media services, lawmakers should focus on what has always been the clearest harm: sexual exploitation by adults. Legislation could start by empowering parents to control who their teens can communicate with. In this sense, the KIDS Act is better than ASAA: it focuses on parents’ access to direct messaging controls rather than approving the installation of each app. Democrats’ alternative bill, the “Safe Messaging for Kids Act,” is still more focused: it would require only that platforms “shall provide a parental tool to allow a parent of a covered user to view the covered user’s direct messaging control settings.” But both bills would require some form of age verification for some adults for lawful content. Paxton doesn’t make that constitutional.
But maybe that’s OK. Do parents really need the government to require platforms and app stores to age-verify users to determine who’s a minor? ASAA requires that a minor’s account “be affiliated with a parental account” but it doesn’t require any effort to prove that the parental account actually belongs to the minor’s parent, because there is no easy or reliable way of doing so. Instead, it’s enough that this account “be established by an individual who the app store provider has determined is an adult.” If we can reasonably assume that person is the parent, why can’t we trust parents to manage the settings on devices they purchase for their teens? After all, mobile carriers allow only adults to set up accounts.
If the existing parental controls in operating systems and app stores are inadequate or too hard to use, that’s where regulation should focus. That would be “less restrictive” of speech, in First Amendment terms, than forcing adults to identify themselves. Perhaps parents do need better controls over direct messaging. Apple iOS currently allows parents to control direct messaging but only for built-in apps. But if any controls required by law should be content and viewpoint-neutral, which means that they should work across all apps, lest they become an indirect way for parents to veto teens’ use of particular apps, like TrevorSpace or GiveUsTheFloor.
Whatever the government might require, it has no business protecting teens from “questionable ideological priorities,” even through the indirect means of requiring parental controls. “Whatever the power of the state to control public dissemination of ideas inimical to the public morality, said the Supreme Court long ago, “it cannot constitutionally premise legislation on the desirability of controlling a person’s private thoughts.” That’s true even if that person is a teenager.
Berin Szóka is President of TechFreedom.
ICE Detainment Center Guards Allegedly Set Up Suicide Death Pools [Techdirt]
Say what you will about cops — even the federal ones — but they have nothing on the people charged with guarding people who have been detained or imprisoned. The cruelty of cops is slightly tempered by the fact that anyone with a cell phone, dash cam, or doorbell surveillance device might catch them in the act. It’s not much a deterrent (and it’s a far better deterrent than police body cameras, ironically enough) but it’s better than the absolute nothing that’s in place in detainment centers, jails, and prisons.
Cops can control their own cameras. Prison guards can control an entire network of cameras. And they’re far more used to dehumanizing people than law enforcement officers on the outside.
So, it’s hardly surprising that the people keeping an eye on the thousands of migrants being imprisoned indefinitely by this administration would be the most inhumane. If citizens stuck in prisons are treated like (diseased) cattle at best, the people dumped into ICE detention centers are treated like something even worse: vermin. That’s a loaded term. And I’m using it correctly when speaking about this administration.
The Associated Press has obtained some evidence of the day-to-day oppressive indignities ICE detainees suffer through each day. And from an unlikely source: 911 calls placed by detainment center staff. Things have to be particularly horrific for guards to consider calling 911 for help.
And they are:
The calls to 911 poured in from staff at Camp East Montana in Texas, the nation’s largest U.S. Immigration and Customs Enforcement detention facility, at a rate of nearly one a day for five months, each its own tale of pain and despair.
A man sobs after being assaulted by another detainee. Another bangs his head against the wall after expressing suicidal thoughts. A pregnant woman complained of severe back pain and also had coronavirus.
Even worse is what’s been said by the detainees. Welcome to the Trump’s brave new world, where bigoted anti-migrant enforcement is now coupled with the potentially deadly effects of this administration’s anti-vax healthcare stance:
The detainees describe a camp where an average of about 3,000 people have lived per day in loud and unsanitary quarters, diseases spread easily and sleep is a luxury. The center will be closed to visitors until at least March 19 because of a measles outbreak, according to U.S. Rep. Veronica Escobar.
That’s mass inhumanity, aided and abetted by an administration that doesn’t care how many people die so long as it can claim some sort of revenge over COVID-19 policies put in place in the last year of Trump’s previous presidential term.
Here’s the more selective inhumanity, which isn’t any better:
At one point [detainee Owen Ramsingh] said he overheard a security guard talking about bets made among the staff over which detainee would be next to die by suicide. The guard said he had paid $500 into a pool, with the total pot riding on the outcome. The talk was particularly jarring, he said, because he had contemplated suicide himself.
Some of you might be saying to yourselves “Well, that’s just something one guy said.” And that’s true, it’s just one guy saying this. But this is also just one guy saying this:
The DHS spokesperson said Ramsingh’s account was false, though provided no indication of how the agency had sought to verify that.
True or not, these are the facts on the ground in Camp East Montana:
Ramsingh said he heard of the betting pool after Jan. 3, when ICE said security guards responded after a 55-year-old Cuban man tried to harm himself and then used handcuffs and force to restrain him. A medical examiner ruled that Geraldo Lunas Campos’s death was a homicide caused by asphyxia.
On Jan. 14, staff reported that a 36-year-old Nicaraguan man died by suicide days after he was detained while working in Minnesota.
Given what we know about what’s happening in this detainment center, coupled with what we know about the historical sadism of “screws,” this doesn’t seem that far-fetched. Then there are the 911 calls — placed by the guards themselves — that made it clear at least six other detainees had attempted or considered attempting suicide during that same time period.
So, while it could just be some guy saying something, consider this: the DHS has more to gain from denying this than Ramsingh — who has already been deported — has to gain from making this allegation.
I don’t find this allegation unbelievable. It seems like exactly the sort of thing people trained and encouraged to treat detainees as less than human would do, especially when suicides and suicidal ideation are a daily occurrence. The government contractors employing them are profiting from human misery. Why shouldn’t they?
Daily Deal: The Courses Digest, Labs Digest, and Exams Digest Bundle [Techdirt]
The Courses Digest, Labs Digest, and Exams Digest Bundle gives you unlimited access to expertly crafted online courses, interactive labs and study tools. Whether you’re aiming for industry-recognized certifications or expanding your tech expertise, this bundle will help you get there with courses on CompTIA, AWS, Microsoft, Cisco, Salesforce, and more. It’s on sale for $70 for a very limited time.
Note: The Techdirt Deals Store is powered and curated by StackCommerce. A portion of all sales from Techdirt Deals helps support Techdirt. The products featured do not reflect endorsements by our editorial team.
03:00 AM
Considering infinity [Seth Godin's Blog on marketing, tribes and respect]
Endless, unlimited and more. These are building blocks of capitalism.
Starbucks knows that they can’t get you to drink three coffees every morning, but their stock price is built on the idea that they can continue to get more customers and make more money from each one.
The Wedding-Industrial complex is built on the simple idea that your wedding should cost the same as your best friend’s wedding did (plus a little more).
The status ratchet is real, and it’s easy to be seduced by it. “Compared to what” is a fundamental component of marketing.
One reason this works is that a little progress gets you positive feedback, which makes you eager to find a little more, a cycle that doesn’t end. Infinity, all the way up.
And, for those seeking social change, the opposite is worth noting:
When asking for penance, self-control and good behavior, infinity is not a useful tool. When someone shows up and tries to do better, “that’s not good enough,” is not a particularly useful motivator.
The useful process begins by earning enrollment in the journey toward better, but it’s not amplified by our criticism of each action being imperfect.
Go-up infinity is about ‘more.’ But too often, social-good infinity is about ‘pure’. And pure is difficult to embrace, because anything less than pure feels like failure.
The Government Told Courts It Could Easily Refund Unlawful Tariffs. Now It Says It Can’t. [Techdirt]
When companies sued to block Trump’s IEEPA tariffs last year, one of the key arguments they made was obvious: if these tariffs turn out to be illegal, we’ll never get our money back. We need an injunction now. The government had an equally confident response: relax, if the tariffs are struck down, we’ll just issue refunds. No big deal. No injunction needed.
Multiple courts bought it. And now, with the Supreme Court having ruled the tariffs unlawful and a judge ordering the refunds, CBP is telling the court that it actually can’t comply with the order. The promises that defeated all those injunctions? Turns out nobody bothered to check whether they were actually true.
Once again, courts trusted what the government told them. Once again, it turns out they were wrong.
Let’s rewind to see how we got here.
Back in April 2025, when importers like V.O.S. Selections were seeking a preliminary injunction to stop the tariffs from being collected, the Department of Justice told the Court of International Trade there was simply no need for such drastic relief. In its brief opposing the injunction, the DOJ was explicit:
And, even if future entries are liquidated, defendants do not intend to oppose the Court’s authority to order reliquidation of entries of merchandise subject to the challenged tariffs if the tariffs are found in a final and unappealable decision to have been unlawfully collected. Such reliquidation would result in a refund of all duties determined to be unlawfully assessed, with interest.
No injunction needed! Refunds would flow. With interest, even. The government repeated this refund promise in case after case after case. In the Learning Resources stay motion, the government told the D.C. district court that there was no risk at all that the government wouldn’t repay:
For any plaintiff who is an importer, even if a stay is entered and defendants do not prevail on appeal, plaintiffs will assuredly receive payment on their refund with interest. “[T]here is virtually no risk” to any importer that they “would not be made whole” should they prevail on appeal. See Sunpreme v. United States, 2017 WL 65421, at *5 (Ct. Int’l Trade Jan. 5, 2017). The most “harm” that could incur would be a delay in collecting on deposits. This harm is, by definition, not irreparable.
In the Axle case, same thing.
In any event, were Axle to ultimately prevail, it could receive a refund of duties paid that would otherwise be eligible for duty-free treatment under the de minimis exemption on any unliquidated entries. 28 U.S.C. §§ 2643-44. To the extent any future entries are liquidated, the Court may order reliquidation of entries subject to the challenged de minimis exemption if the duties paid by Axle are, in a final and unappealable decision, found to have been unlawfully collected. Such reliquidation would result in a refund of all duties determined to be unlawfully assessed, with interest.
In the Princess Awesome joint stipulation, the government formally agreed that there was nothing to fear about getting repaid:
Defendants stipulate that they will not oppose the Court’s authority to order reliquidation of entries of merchandise subject to the challenged IEEPA duties and that they will refund any IEEPA duties found to have been unlawfully collected, after a final and unappealable decision has been issued finding the duties to have been unlawfully collected
And the courts relied on these representations. In December 2025, when AGS Company Automotive Solutions sought a preliminary injunction to stay the liquidation of its entries, the three-judge panel denied the motion specifically because of the government’s refund promises:
For the reasons stated above, we conclude that the Government has taken the “unequivocal position” that “liquidation will not affect the availability of refunds after a final decision” in V.O.S. Gov’t Resp. at 2–3. The Government would be judicially estopped from “assum[ing] a contrary position” in the future.
Note the court’s foresight here. The panel explicitly invoked judicial estoppel—basically saying “okay, now that you’ve said this to a court, you’re bound by it going forward.” You get the sense that the court had a sense of where all this was going.
Then the Supreme Court ruled 6-3 in Learning Resources, Inc. v. Trump that the IEEPA tariffs were unlawful. Judge Eaton at the Court of International Trade—designated as the sole judge to handle IEEPA refund cases—last week ordered CBP basically pay back everyone who paid an IEEPA tariff. Everyone. Not just those who sued.
In court, when the DOJ pushed back a bit, Eaton was blunt:
“Customs knows how to do this,” Eaton said during a court hearing on Wednesday. “They do it every day. They liquidate entries and make refunds.”
Enter the declaration of Brandon Lord, CBP’s Executive Director of the Trade Programs Directorate, filed the day after Judge Eaton’s order. He points out that, actually, there are a TON of tariffs to repay.
As of March 4, 2026, over 330,000 importers have made a total of over 53 million entries in which they have deposited or paid duties imposed pursuant to the International Emergency Economic Powers Act (“IEEPA”), 50 U.S.C. § 1701 et seq. (the “subject entries”). As of March 4, 2026, the total amount of IEEPA duties and estimated duty deposits collected pursuant to IEEPA is approximately $166 billion. Approximately 20.1 million entries remain unliquidated as of March 4, 2026.
And, apparently, it turns out that CBP is not at all prepared to repay what it owes:
In light of the Court’s March 5, 2026 amended order, CBP is now facing an unprecedented volume of refunds. Its existing administrative procedures and technology are not well suited to a task of this scale and will require manual work that will prevent personnel from fully carrying out the agency’s trade enforcement mission. Personnel would be redirected from responsibilities that serve to mitigate imminent threats to national security and economic security.
Lord’s declaration lays out a big list of technical and logistical obstacles. CBP’s Automated Commercial Environment (ACE) system can apparently only batch-process 10,000 entry summary lines at a time, and there are over 1.6 billion entry summary lines that need updating. Importers frequently lumped their IEEPA duties together with other duties on the same line, meaning CBP personnel would have to manually untangle the amounts. Processing each individual refund takes about 5 minutes, which across 53 million entries works out to over 4.4 million hours.
There’s also a mess involving different entry types and automatic liquidation timelines—Lord’s declaration goes into a bunch of technical details about “formal” vs. “informal” entries, claiming that 4 million entries will automatically process next week and “CBP does not have a process to prevent” it. Even if the legal details are deep in the weeds, the message is clear: even with the Supreme Court ruling in hand, CBP claims parts of this train are still moving and they can’t stop it.
CBP says it can build new ACE functionality in 45 days that would streamline the process. The proposed system actually sounds reasonable. Which makes it worse: if you spent the better part of a year telling every court that would listen that refunds were totally manageable, that there was “virtually no risk” importers wouldn’t be made whole, that “such reliquidation would result in a refund of all duties determined to be unlawfully assessed, with interest”—then maybe, just maybe, you should have spent some of that year building the system to actually do it? Send over a DOGE bro or two to vibe code up a solution?
The Supreme Court case wasn’t a surprise. The government was a party to it. They knew the ruling was coming. They knew that if they lost, refunds would be necessary on a massive scale. And even just based on how the oral arguments went, they should have known how this would turn out.
Instead, CBP appears to have done absolutely nothing to prepare. The government used the promise of easy refunds as a sword to defeat injunction after injunction, convincing courts that importers would suffer no irreparable harm because the money could always be returned. Having successfully avoided those injunctions—allowing the tariffs to keep being collected for months on end, swelling that $166 billion pot—the government now tells the court that returning the money is an operational nightmare that requires new technology it hasn’t built yet.
This is exactly the scenario the AGS panel warned about. And if the government tries to argue that it can’t provide refunds—rather than that it just needs more time—it will run headlong into the judicial estoppel doctrine that the court already set up like a tripwire. As the AGS panel put it, quoting the Supreme Court: “where a party assumes a certain position in a legal proceeding, and succeeds in maintaining that position, he may not thereafter, simply because his interests have changed, assume a contrary position.”
Every month the government successfully avoided an injunction was another month it kept collecting tariffs. That $166 billion didn’t accumulate by accident. The government had every incentive to promise easy refunds and zero incentive to actually prepare for them. The longer importers waited for relief, the bigger the pot grew.
And now, with the Supreme Court having ruled those tariffs illegal, and with courts having explicitly warned that the government would be judicially estopped from changing its position, CBP says it needs 45 days to build new software before it can start writing checks.
“Customs knows how to do this,” Judge Eaton said. “They do it every day.”
Maybe. But apparently nobody in the entire federal government thought to ask whether CBP could actually deliver on the promises DOJ was making to court after court after court. Either that, or they just didn’t care what the answer was.
Pluralistic: Billionaires are a danger to themselves and (especially) us (09 Mar 2026) [Pluralistic: Daily links from Cory Doctorow]
->->->->->->->->->->->->->->->->->->->->->->->->->->->->->
Top Sources:
None
-->

Today's links
- Billionaires are a danger to themselves and (especially) us: A billionaire is a machine for producing policy failures at scale.
- Hey look at this: Delights to delectate.
- Object permanence: Librarians Against DRM; Copyright maximalist MP is a pirate; "The Monster"; The perversity of self-destructing ebooks; Space opera cliches; Social software politics; Game in a browser's location bar; Map of sf/f; Group chat sucks; Jeep hack; Gandersauce.
- Upcoming appearances: Where to find me.
- Recent appearances: Where I've been.
- Latest books: You keep readin' em, I'll keep writin' 'em.
- Upcoming books: Like I said, I'll keep writin' 'em.
- Colophon: All the rest.
Billionaires are a danger to themselves and (especially) us (permalink)
Even if rich people were no more likely to believe stupid shit than you or me, it would still be a problem. After all, I believe in my share of stupid shit (and if you think that none of the shit you believe in is stupid, then I'm afraid we've just identified at least one kind of stupid shit you believe in).
The problem isn't whether rich people believe stupid shit; it's the fact that when a rich person believes something stupid, that belief can turn into torment for dozens, thousands, or millions of people.
Here's a historical example that I think about a lot. In 1928, Henry Ford got worried about the rubber supply chain. All the world's rubber came from plantations in countries that he had limited leverage over and he was worried that these countries could kneecap his operation by cutting off the supply. So Ford decided he would start cultivating rubber in the Brazilian jungles, judging that Brazil's politicians were biddable, bribeable or bludgeonable and thus not a risk.
Ford took over a large area of old-growth jungle in Brazil and decreed that a town be built there. But not just any town: Ford decreed that the town of Fordlandia would be a replica of Dearborn, the company town he controlled in Michigan. Now, leaving aside the colonialism and other ethical considerations, there are plenty of practical reasons not to replicate Dearborn, MI on the banks of the Rio Tapajós.
For one thing, Brazil is in the southern hemisphere, and Dearborn is in the northern hemisphere. The prefab houses that Ford ordered for Fordlandia had windows optimized for southern exposure, which is the normal way of designing a dwelling in the northern hemisphere. In the southern hemisphere, you try and put your windows on the other side of the building.
Ford's architects told him this, and proposed having the factory flip the houses' orientation. But Ford was adamant: he'd had a vision for a replica of his beloved Dearborn plunked down smack in the middle of the Amazon jungle, and by God, that was what he would get:
Fordlandia was a catastrophe for so many reasons, and the windows are just a little footnote, but it's a detail that really stuck with me because it's just so stupid. Ford was a vicious antisemite, a bigot, a union-buster and an all-round piece of shit, but also, he believed that his opinions trumped the axial tilt of the planet Earth.
In other words, Henry Ford wasn't merely evil – he was also periodically as thick as pigshit. Ford's cherished stupidities didn't just affect him, they also meant that a whole city full of people in the Amazon had windows facing the wrong direction. Like I said, I sometimes believe stupid things, but those stupid things aren't consequential the way that rich people's cherished stupidities are.
This would be bad enough if rich people were no more prone to stupid beliefs than the rest of us, but it's actually worse than that. When I believe something stupid, it tends to get me in trouble, which means that (at least some of the time), I get to learn from my mistakes. But if you're a rich person, you can surround yourself with people who will tell you that you are right even when you are so wrong, with the result that you get progressively more wrong, until you literally kill yourself:
https://www.scientificamerican.com/article/alternative-medicine-extend-abbreviate-steve-jobs-life/
A rich person could surround themselves with people who tell them that they're being stupid, but in practice, this almost never happens. After all, the prime advantage to accumulating as much money as possible is freedom from having to listen to other people. The richer you are, the fewer people there are who can thwart your will. Get rich enough and you can be found guilty of 34 felonies and still become President of the United States of America.
But wait, it gets even worse! Hurting other people is often a great way to get even more rich. So the richer you get, the more insulated you are from consequences for hurting other people, and the more you hurt other people, the richer you get.
What a world! The people whose wrong beliefs have the widest blast-radius and inflict the most collateral damage also have the fewest sources of external discipline that help them improve their beliefs, and often, that collateral damage is a feature, not a bug.
Billionaires are a danger to themselves and (especially) to the rest of us. They are wronger than the median person, and the consequences of their wrongness are exponentially worse than the consequences of the median person's mistake.
This has been on my mind lately because of a very local phenomenon.
I live around the corner from Burbank airport, a great little regional airport on the edge of Hollywood. It was never brought up to code, so the gates are really close together, which means the planes park really close together, and there's no room for jetways, so they park right up against the terminal. The ground crews wheel staircase/ramps to both the front and back of the plane. That means that you can walk the entire length of the terminal in about five minutes, and boarding and debarking takes less than half the time of any other airport. Sure, if one of those planes ever catches fire, every other plane is gonna go boom, and everyone in the terminal is toast, but my sofa-to-gate time is like 15 minutes.
Best of all, Burbank is a Southwest hub. When we moved here a decade ago, this was great. Southwest, after all, has free bag-check, open seating, a great app, friendly crews, and a generous policy for canceling or changing reservations.
If you fly in the US, you know what's coming next. In 2024, a hedge fund called Elliott Investment Management acquired an 11% stake in SWA, forced a boardroom coup that saw it replace five of the company's six directors, and then instituted a top to bottom change in airline policies. The company eliminated literally everything that Southwest fliers loved about the airline, from the free bags to the open seating:
The airline went from being the least enshittified airline in America to the most. Southwest is now worse than Spirit airlines – no, really. Southwest doesn't just merely charge for seat selection, but if you refuse to pay for seat selection, they preferentially place you in a middle seat even on a half-empty flight, as a way of pressuring you to pay the sky-high junk fee for seat selection:
https://www.reddit.com/r/SouthwestAirlines/comments/1rd2g0k/ngl_thought_yall_were_joking/
Obviously, passengers who are given middle seats (and the passengers around them, who paid for window or aisle seats) don't like this, so they try to change seats. So SWA now makes its flight attendants order passengers not to switch seats, and they've resorted to making up nonsense about "weight balancing":
Even without junk fees, Southwest's fares are now higher than their rivals. I'm flying to San Francisco tomorrow to host EFF executive director Cindy Cohn's book launch at City Lights:
https://citylights.com/events/cindy-cohn-launch-party-for-privacys-defender/
Normally, I would have just booked a SWA flight from Burbank to SFO or Oakland (which gets less fog and is more reliable). But the SWA fare – even without junk fees – was higher than a United ticket out of the same airport, even including a checked bag, seat selection, etc. Southwest is genuinely worse than Spirit now: not only does it have worse policies (forcing occupancy of middle seats!), and more frustrated, angrier flight crew (flight attendants are palpably sick of arguing with passengers), but SWA is now more expensive than United!
All of this is the fault of one billionaire: Elliott Investment Management CEO Peter Singer, one of America's most guillotineable plutes. This one guy personally enshittified Southwest Airlines, along with many other businesses in America and abroad. Because of this one guy, millions of people are made miserable every single day. Singer flogged off his shares and made a tidy profit. He's long gone. But SWA will never recover, and every day until its collapse, millions of passengers and flight attendants will have a shitty day because of this one guy:
Even if Peter Singer were no more prone to ethical missteps than you or me, the fact that he is morbidly wealthy means that his ethical blind spots leave behind a trail of wreckage that rivals a comet. And of course, being as rich as Peter Singer inflicts a lasting neurological injury that makes you incapable of understanding how wrong you are, which means that Peter Singer is doubly dangerous.
Billionaires aren't just a danger when they're trying to make money, either. One of the arguments in favor of billionaires is that sometimes, the "good" billionaires take up charitable causes. But even here, billionaires can cause sweeping harm. Take Bill Gates, whose charitable projects include waging war on the public education system, seeking to replace public schools with charter schools.
Gates has no background in education, but he spent millions on this project. He is one of the main reasons that poor communities around the country have been pressured to shutter their public schools and replace them with weakly regulated, extractive charters:
https://apnews.com/article/92dc914dd97c487a9b9aa4b006909a8c
This was a catastrophe. A single billionaire dilettante's cherished stupidity wrecked the educational chances of a generation of kids:
https://dissidentvoice.org/2026/03/free-market-charter-schools-wreak-havoc-in-michigan/
Gates was a prep-school kid, so it's weird for him to have forceful views about a public education system he never experienced. In reality, it's not so much that Gates has forceful views about schools – rather, he has forceful views about teachers' unions, which he wishes to see abolished. Gates is one of America's most vicious union-busters:
Gates's ideology permeates all of his charitable work. We all know about Gates's work on public health, but less well known is the role that Gates has played in blocking poor countries from exercising their rights under the WTO to override drug patents in times of emergency. In the 2000s, the Gates Foundation blocked South Africa from procuring the anti-retroviral AIDS drugs it was entitled to under the WTO's TRIPS agreement. The Gates Foundation blocked the Access to Medicines WIPO treaty, which would have vastly expanded the Global South's ability to manufacture life-saving drugs. And during the acute phase of the covid pandemic, Gates personally intervened to kill the WHO Covid-19 Technology Access Pool and to get Oxford to renege on its promise to make an open-source vaccine:
https://pluralistic.net/2021/04/13/public-interest-pharma/#gates-foundation
It's not that Gates is insincere in his desire to improve public health outcomes – it's that his desire to improve public health conflicts with his extreme ideology of maximum intellectual property regimes. Gates simply opposes open science and compulsory licenses on scientific patents, even when that kills millions of people (as it did in South Africa). Gates's morbid wealth magnifies his cherished stupidities into weapons of mass destruction.
Gates is back in the news these days because of his membership in the Epstein class. Epstein is the poster child for the ways that wealth is a force-multiplier for bad ideas. We can't separate Epstein's sexual predation from his wealth. Epstein spun elaborate junk-science theories to justify raping children, becoming mired in that most rich-guy coded of quagmires, eugenics:
https://www.statnews.com/2026/02/24/epstein-cell-line-george-church-harvard-personal-genome-project/
Epstein openly discussed his plans to seed the planet with his DNA, reportedly telling one scientist that he planned to fill his ranch with young trafficked girls and to keep 20 of them pregnant with his children at all times:
https://www.nytimes.com/2019/07/31/business/jeffrey-epstein-eugenics.html
We still don't know where Epstein's wealth came from, but we know that he was a central node in a network of vast riches, much of which he directed to his weird scientific projects. That network also protected him from consequences for his prolific child-rape project, which had more than 1,000 survivors.
In embracing eugenics junk science, Epstein was ahead of the curve. Today, eugenics is all the rage, reviving an idea that went out of fashion shortly after the Fordlandia era. After all, Henry Ford didn't just build a private city where his word was law – he also bought up media companies to promote his ideas of racial superiority:
https://en.wikipedia.org/wiki/The_Dearborn_Independent
Despite being too cringe to make it onto Epstein island, Elon Musk is the standard bearer for the dangers of billionaireism:
Like Henry Ford, he craves company towns where his word is law:
https://www.texasmonthly.com/news-politics/inside-starbase-spacex-elon-musk-company-town/
Like Ford, he buys up media companies and then uses them to push his batshit ideas about racial superiority:
https://www.motherjones.com/politics/2025/01/eugenics-isnt-dead-its-thriving-in-tech/
Like Peter Singer, he is a master enshittifier who never met a junk fee he didn't fall in love with:
https://edition.cnn.com/2022/11/01/tech/musk-twitter-verification-price
And like Epstein, he wants to seed the human race with his babies, and has built a secret compound in the desert he plans to fill with women he has impregnated:
https://www.realtor.com/news/celebrity-real-estate/elon-musk-compound-austin-children/
Billionaires and their lickspittles will tell you that all of this is wrong: the market selects "capital allocators" by executing a vast, distributed computer program whose logic gates are every producer and consumer in The Economy (TM), and whose data are trillions of otherwise uncomputable buy and sell decisions.
This is a tautology: the argument goes that only good people are made rich, and therefore all the rich people are good. If rich people had as many cherished stupidities as I claim, The Economy (TM) would relieve them of their wealth, and thus their power to allocate capital, and thus their potential to hurt people by being wrong, which means that they must be right.
This is the stupidest (and most destructive) of all of billionaireism's cherished stupidities: that we live in a meritocracy, which means that whatever the richest people want must be right. It's a modern update to the doctrine of divine providence, which held that we can discern god's favor through wealth. The more god loves you, the richer he makes you.
This can't be true, because every single economic cataclysm in the history of the world was the fault of rich people. Rich people gave us the 19th century's bank panics. They gave us the South Seas bubble. They gave us the Great Depression, and the S&L Crisis, and the Great Financial Crisis. They invented greedflation and created the cost of living crisis. Today, they are teeing up an AI crash that will make 2008 look like the best day of your life:
https://pluralistic.net/2025/12/05/pop-that-bubble/#u-washington
The old left aphorism has it that "every billionaire is a policy failure." That's true, but it's incomplete. Every billionaire is a machine for producing policy failures at scale.
(Image: Aude, CC BY 4.0, modified)
Hey look at this (permalink)

- How Live Nation allegedly terrorized the concert industry https://www.theverge.com/report/891241/live-nation-ticketmaster-week-one-jury-trial
-
Canada's One-Man Air Force – and His Calculated Airline Crusade https://www.donotpassgo.ca/p/canadas-one-man-air-force-and-his
-
Cloud Sovereignty Framework Self Assessment https://www.suse.com/cloud-sovereignty-framework-assessment/
-
EFF, Ubuntu and Other Distros Discuss How to Respond to Age-Verification Laws https://linux.slashdot.org/story/26/03/09/0544224/eff-ubuntu-and-other-distros-discuss-how-to-respond-to-age-verification-laws
-
Reading “The Ethnography of Infrastructure” https://www.not-so-obvious.net/reading-the-ethnography-of-infrastructure/
Object permanence (permalink)
#20yrsago Indie label uses heartfelt note instead of copy-restriction http://blog.resonancefm.com/archives/48
#20yrsago Clay Shirky’s ETECH presentation on the politics of social software https://craphound.com/youshutupetech2006.txt
#20yrsago Judge quotes Adam Sandler movie in decision blasting defendant https://www.thesmokinggun.com/documents/crime/motion-denied-because-youre-idiot
#15yrsago Video game in your browser’s location bar web.archive.org/web/20110309212313/http://probablyinteractive.com/url-hunter
#15yrsago Wondrous, detailed map of the history of science fiction https://web.archive.org/web/20110310152548/http://scimaps.org/submissions/7-digital_libraries/maps/thumbs/024_LG.jpg
#15yrsago American Library Association task forces to take on ebook lending https://web.archive.org/web/20110310085634/https://www.wo.ala.org/districtdispatch/?p=5749
#15yrsago Wisconsin capitol bans recording, flags, reading, balloons, chairs, bags, backpacks, photography, etc etc etc https://captimes.com/news/local/govt-and-politics/more-rules-released-for-state-capitol-visitors/article_f044044f-6183-5128-b718-d5dffbfdb573.html
#15yrsago Librarians Against DRM logo https://web.archive.org/web/20110308170030/https://readersbillofrights.info/librariansagainstDRM
#15yrsago Extinct invertebrates caught in a 40 million year old sex act https://web.archive.org/web/20110303234001/http://news.discovery.com/animals/40-million-year-old-sex-act-captured-in-amber.html
#15yrsago Improvised toilets of earthquake-struck Christchurch https://web.archive.org/web/20110310044912/https://www.showusyourlongdrop.co.nz/
#15yrsago Canadian MP who shills for the record industry is an enthusiastic pirate https://web.archive.org/web/20110310163136/https://www.michaelgeist.ca/content/view/5673/125/
#15yrsago The Monster: the fraud and depraved indifference that caused the subprime meltdown https://memex.craphound.com/2011/03/07/the-monster-the-fraud-and-depraved-indifference-that-caused-the-subprime-meltdown/
#15yrsago Self-destructing ebooks: paper’s fragility is a bug, not a feature https://www.theguardian.com/technology/2011/mar/08/ebooks-harpercollins-26-times
#10yrsago Senior U.S. immigration judge says 3 and 4 year old children can represent themselves in court https://web.archive.org/web/20160304201631/http://www.thestar.com/news/world/2016/03/04/us-judge-says-3-and-4-year-olds-can-represent-themselves-in-immigration-court.html
#10yrsago Crimefighting for fun and profit: data-mining Medicare fraud and likely whistleblowers https://www.wired.com/2016/03/john-mininno-medicare/
#10yrsago Extensive list of space opera cliches https://www.antipope.org/charlie/blog-static/2016/03/towards-a-taxonomy-of-cliches-.html
#10yrsago Verizon pays $1.35M FCC settlement for using “supercookies” https://web.archive.org/web/20160308111653/https://motherboard.vice.com/read/verizon-settles-over-supercookies
#10yrsago Group chat: “an all-day meeting with random participants and no agenda” https://signalvnoise.com/svn3/is-group-chat-making-you-sweat/#.1chnl7hf4
#10yrsago Less than a year on, America has all but forgotten the epic Jeep hack https://www.wired.com/2016/03/survey-finds-one-4-americans-remembers-jeep-hack/
#10yrsago Racial justice organizers to FBI vs Apple judge: crypto matters to #blacklivesmatter https://theintercept.com/2016/03/08/the-fbi-vs-apple-debate-just-got-less-white/
#1yrago Gandersauce https://pluralistic.net/2025/03/08/turnabout/#is-fair-play
Upcoming appearances (permalink)

- San Francisco: Launch for Cindy Cohn's "Privacy's Defender" (City Lights), Mar 10
https://citylights.com/events/cindy-cohn-launch-party-for-privacys-defender/ -
Barcelona: Enshittification with Simona Levi/Xnet (Llibreria Finestres), Mar 20
https://www.llibreriafinestres.com/evento/cory-doctorow/ -
Berkeley: Bioneers keynote, Mar 27
https://conference.bioneers.org/ -
Montreal: Bronfman Lecture (McGill) Apr 10
https://www.eventbrite.ca/e/artificial-intelligence-the-ultimate-disrupter-tickets-1982706623885 -
London: Resisting Big Tech Empires (LSBU)
https://www.tickettailor.com/events/globaljusticenow/2042691 -
Berlin: Re:publica, May 18-20
https://re-publica.com/de/news/rp26-sprecher-cory-doctorow -
Berlin: Enshittification at Otherland Books, May 19
https://www.otherland-berlin.de/de/event-details/cory-doctorow.html -
Hay-on-Wye: HowTheLightGetsIn, May 22-25
https://howthelightgetsin.org/festivals/hay/big-ideas-2
Recent appearances (permalink)
- Chicken Mating Harnesses (This Week in Tech)
https://twit.tv/shows/this-week-in-tech/episodes/1074 -
The Virtual Jewel Box (U Utah)
https://tanner.utah.edu/podcast/enshittification-cory-doctorow-matthew-potolsky/ -
Tanner Humanities Lecture (U Utah)
https://www.youtube.com/watch?v=i6Yf1nSyekI -
The Lost Cause
https://streets.mn/2026/03/02/book-club-the-lost-cause/ -
Should Democrats Make A Nuremberg Caucus? (Make It Make Sense)
https://www.youtube.com/watch?v=MWxKrnNfrlo
Latest books (permalink)
- "Canny Valley": A limited edition collection of the collages I create for Pluralistic, self-published, September 2025 https://pluralistic.net/2025/09/04/illustrious/#chairman-bruce
-
"Enshittification: Why Everything Suddenly Got Worse and What to Do About It," Farrar, Straus, Giroux, October 7 2025
https://us.macmillan.com/books/9780374619329/enshittification/ -
"Picks and Shovels": a sequel to "Red Team Blues," about the heroic era of the PC, Tor Books (US), Head of Zeus (UK), February 2025 (https://us.macmillan.com/books/9781250865908/picksandshovels).
-
"The Bezzle": a sequel to "Red Team Blues," about prison-tech and other grifts, Tor Books (US), Head of Zeus (UK), February 2024 (thebezzle.org).
-
"The Lost Cause:" a solarpunk novel of hope in the climate emergency, Tor Books (US), Head of Zeus (UK), November 2023 (http://lost-cause.org).
-
"The Internet Con": A nonfiction book about interoperability and Big Tech (Verso) September 2023 (http://seizethemeansofcomputation.org). Signed copies at Book Soup (https://www.booksoup.com/book/9781804291245).
-
"Red Team Blues": "A grabby, compulsive thriller that will leave you knowing more about how the world works than you did before." Tor Books http://redteamblues.com.
-
"Chokepoint Capitalism: How to Beat Big Tech, Tame Big Content, and Get Artists Paid, with Rebecca Giblin", on how to unrig the markets for creative labor, Beacon Press/Scribe 2022 https://chokepointcapitalism.com
Upcoming books (permalink)
- "The Reverse-Centaur's Guide to AI," a short book about being a better AI critic, Farrar, Straus and Giroux, June 2026
-
"Enshittification, Why Everything Suddenly Got Worse and What to Do About It" (the graphic novel), Firstsecond, 2026
-
"The Post-American Internet," a geopolitical sequel of sorts to Enshittification, Farrar, Straus and Giroux, 2027
-
"Unauthorized Bread": a middle-grades graphic novel adapted from my novella about refugees, toasters and DRM, FirstSecond, 2027
-
"The Memex Method," Farrar, Straus, Giroux, 2027
Colophon (permalink)
Today's top sources:
Currently writing: "The Post-American Internet," a sequel to "Enshittification," about the better world the rest of us get to have now that Trump has torched America ( words today, total)
- "The Reverse Centaur's Guide to AI," a short book for Farrar, Straus and Giroux about being an effective AI critic. LEGAL REVIEW AND COPYEDIT COMPLETE.
-
"The Post-American Internet," a short book about internet policy in the age of Trumpism. PLANNING.
-
A Little Brother short story about DIY insulin PLANNING

This work – excluding any serialized fiction – is licensed under a Creative Commons Attribution 4.0 license. That means you can use it any way you like, including commercially, provided that you attribute it to me, Cory Doctorow, and include a link to pluralistic.net.
https://creativecommons.org/licenses/by/4.0/
Quotations and images are not included in this license; they are included either under a limitation or exception to copyright, or on the basis of a separate license. Please exercise caution.
How to get Pluralistic:
Blog (no ads, tracking, or data-collection):
Newsletter (no ads, tracking, or data-collection):
https://pluralistic.net/plura-list
Mastodon (no ads, tracking, or data-collection):
Bluesky (no ads, possible tracking and data-collection):
https://bsky.app/profile/doctorow.pluralistic.net
Medium (no ads, paywalled):
https://doctorow.medium.com/
https://twitter.com/doctorow
Tumblr (mass-scale, unrestricted, third-party surveillance and advertising):
https://mostlysignssomeportents.tumblr.com/tagged/pluralistic
"When life gives you SARS, you make sarsaparilla" -Joey "Accordion Guy" DeVilla
READ CAREFULLY: By reading this, you agree, on behalf of your employer, to release me from all obligations and waivers arising from any and all NON-NEGOTIATED agreements, licenses, terms-of-service, shrinkwrap, clickwrap, browsewrap, confidentiality, non-disclosure, non-compete and acceptable use policies ("BOGUS AGREEMENTS") that I have entered into with your employer, its partners, licensors, agents and assigns, in perpetuity, without prejudice to my ongoing rights and privileges. You further represent that you have the authority to release me from any BOGUS AGREEMENTS on behalf of your employer.
ISSN: 3066-764X
Monday 2026-03-09
11:00 PM
If You’re Going To Defend AI And Whine About Its Critics, You Should Probably Be Honest About Its Actual Harms [Techdirt]
I think this recent post by AI industry CEO Matt Shumer is worth a read. In it, he basically explains how quickly LLMs (large language models) are evolving to supplant many developers and programmers, and how that disruption is coming to other industries quickly. He also warns critics of AI to adjust their priors and realize the AI tools you mocked just six months ago, aren’t the ones in use today:
“I am no longer needed for the actual technical work of my job. I describe what I want built, in plain English, and it just… appears. Not a rough draft I need to fix. The finished thing. I tell the AI what I want, walk away from my computer for four hours, and come back to find the work done. Done well, done better than I would have done it myself, with no corrections needed. A couple of months ago, I was going back and forth with the AI, guiding it, making edits. Now I just describe the outcome and leave.”
While the post is interesting (with the understanding this is somebody making and selling automation software), you might notice something: absolutely nowhere in the blog post does he meaningfully acknowledge the widespread problems with existing AI use. Either because his financial self-interest doesn’t allow for honest acknowledgment of them, or because he simply doesn’t find those aspects all that interesting.
Maybe both.
There’s no mention of how these tools are causing corporations to blow past their already tepid climate goal; no mention of how the affluent, surveillance-obsessed exec dictating its trajectory enthusiastically cozied up to fascists; no mention of how Elon Musk and Mark Zuckerberg’s data centers are funneling pollution directly into black neighborhoods; zero mention of the technofascist plan to leverage AI to decimate unions; no mention of the weird and precarious financial shell games powering the sector.
This New York Times article from a couple weeks ago is probably a better example of this art form. It’s an article, ostensibly about why the public has been so hostile to AI, that takes until the THIRTY-EIGHTH paragraph to actually try and explain some of the reasons. And even then it’s kind of a throwaway paragraph that doesn’t wrestle seriously with any of the criticism:
“The tech executives who are betting their companies’ futures on the triumph of A.I. have many resources to make sure it happens. They can spend even more money to build even more data centers. On the other hand, data centers around the country are increasingly a target of opposition for local residents who dislike the noise, the disruption, the secrecy and the lack of community benefits like jobs.”
Distilling the animosity against AI as just some random grumbling about “noise” and ambiguous “disruption” is a very weird and conscious choice, and I’d argue that this minimization, a reflection of the establishment press’ need to appease and protect access to corporate power, is itself a major contributor to growing hostility toward AI.
The fact that much of the public animosity to AI may be linked to the fact that its salesmen have overtly and enthusiastically enabled fascism just isn’t mentioned. The Times doesn’t think that’s relevant.
The fact that many U.S. billionaires see AI largely as a way to lazily cut corners and obliterate unions (see: its rushed adoption in journalism outlets like the LA Times or Politico) isn’t mentioned either. That the goal for most AI executives is to power this latest technological revolution completely free of any corporate oversight whatsoever? Again, somehow not deemed relevant.
Stories like this cling to a narrative that vaguely imply people are generally angry about AI due to some ambiguous flaw in their “perception,” likely caused by the way AI is being portrayed to the public on the tee vee:
“The A.I. companies seem increasingly alert to a perception problem. This year’s Super Bowl featured A.I.-themed ads that were defensive or just odd. Amazon’s ad showed A.I. proposing ways to kill Chris Hemsworth. The twist at the end: A.I. disarms him with a promised massage.”
And while there certainly are people who are intractably hostile to all aspects of automation and simply refuse to engage with it on any level (including understanding it), a huge swath of the animosity is being driven by historic and justified anger at the extraction class.
That anger and energy is good, and just, and will likely serve us well in the months and years to come. I’d argue it deserves a wide berth; including by tech industry insiders and AI advocates who don’t want to live under permanent kakistocracy staffed by weird zealots who operate at a third-grade reading level, openly enthusiastic about their grand visions for a permanent mass-surveillance murder autocracy.
Stories like this Times piece will often fixate on the AI “doomer narrative” (SkyNet will kill us all), but downplay that this specific strain of doomerism (very often pushed by wealthy industry insiders), often exists to both misrepresent what LLMs are capable of, but also to direct attention away from more realism-based criticism the industry doesn’t really want to talk about.
That’s not to say people can’t or shouldn’t be excited by evolutions in automation. But it is to say if you’re an AI advocate and you’re not also talking seriously about the very valid reasons so many people are pissed off, you’re not really talking seriously about the subject at all. You’re in marketing.
09:00 PM
Major Publishers Sue Anna’s Archive Over ‘Staggering’ Copyright Infringement, Seek Injunction [TorrentFreak]
 Anna’s Archive has already faced its fair share of legal trouble and domain name problems this year.
Anna’s Archive has already faced its fair share of legal trouble and domain name problems this year.
The popular shadow library was sued by Spotify and several major record labels in late December and lost many of its domain names.
The site responded by adding new domain names. After losing its .LI domain last week, it added .VG,.PK, and .GD as new alternatives. However, this does not mean that the pressure is fading. Within a matter of days, the .VG domain was already suspended by the domain registrar.
63 Million Pirated Books
After watching the music industry’s legal push, a group of thirteen major publishers has also sprung into action. In a complaint filed at a New York federal court last week, they accuse Anna’s Archive of staggering copyright infringement by hosting 63 million books and 95 million papers, most of which are pirated.
“Defendants shamelessly describe themselves as a collection of ‘pirates’ not ‘bound by the law’,” the complaint reads.
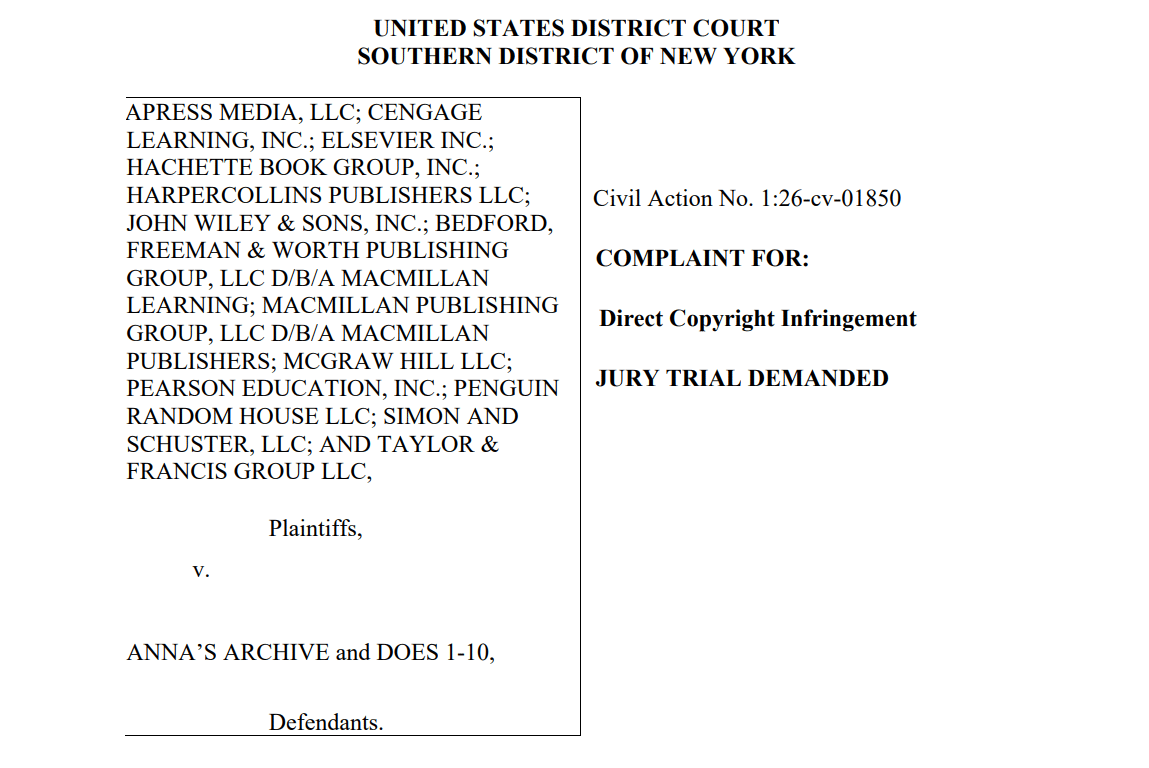
The publishers highlight that the site facilitated 763,000 downloads per day last Tuesday, as reported by the site’s own statistics. These downloads are predominantly unauthorized, they add.
“Plaintiffs are not aware that any of the copyright-protected works on Anna’s Archive are licensed or authorized by the copyright owners; to the contrary, their reproduction and distributions are blatantly illegal infringements,” the complaint notes.
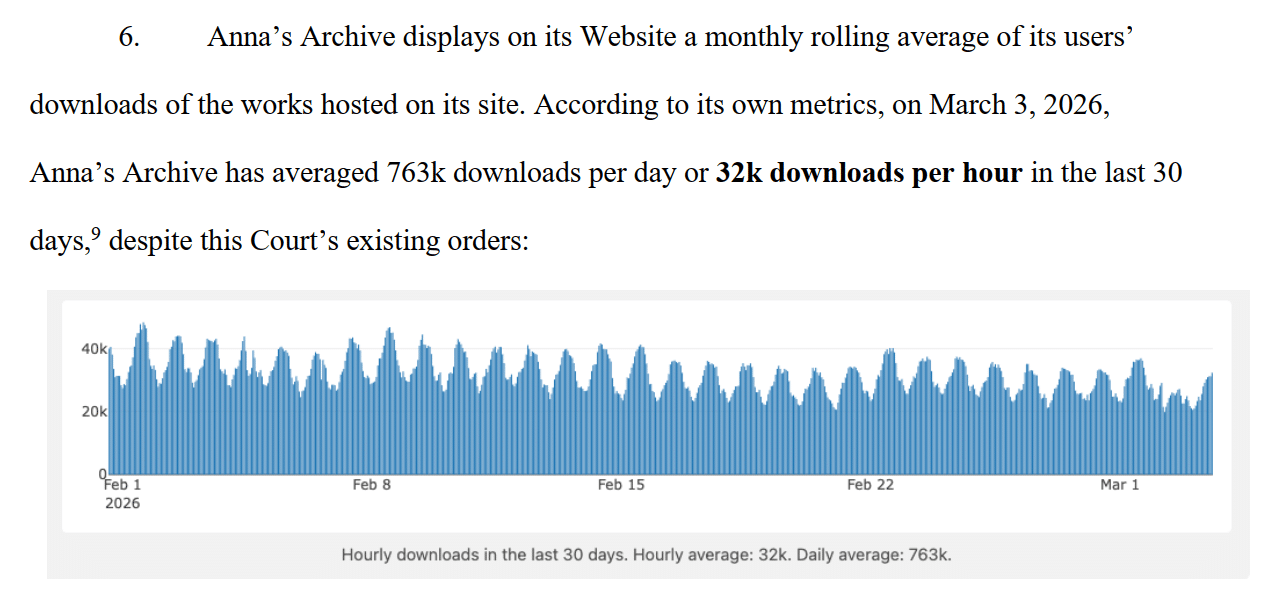
The publishers also highlight the AI training angle. They note that the shadow library provided high-speed access to 140+ million texts to LLM developers in China, Russia, and elsewhere. This includes a blog post titled “If You’re an LLM, Please Read This” which specifically targets AI companies.
The complaint alleged that Anna’s Archive reportedly charges significant fees for premium access, citing a LinkedIn post that mentioned a $200,000 donation.
“The amount of the ‘enterprise-level donation’ is not specified on the Website but it is reported to be $200,000. In an e-mail exchange with a researcher inquiring about the cost of the collection for AI training, Anna’s Archive offered premium access for $200,000,” the complaint notes.

The Injunction is Key
With 130 copyrighted works mentioned in the complaint, and damages up to $150,000 per infringed work, the publishers seek up to $19.5 million in compensation. However, with the site’s operators being unknown and unreachable, chances are slim that this amount will be paid.
The publishers are aware of this. In fact, if we carefully read the framing of their complaint, it appears that the legal action is predominantly intended to target domain names and other technical infrastructure of Anna’s Archive.
In recent weeks, the music industry injunction in the Atlantic/Spotify case has helped to take out several domain names. However, Anna’s Archive has since removed music-related content from the site. Therefore, the publishers now seek a similar injunction.
“Were the Defendants to repost the contents of its illegal repository of stolen works without these audio files, the Atlantic Order would still be satisfied. Nor can the publisher Plaintiffs in this case enforce the Atlantic Order to protect their own copyrights,” the complaint reads.
Injunction Targeting Hosts, Registrars, and Registries
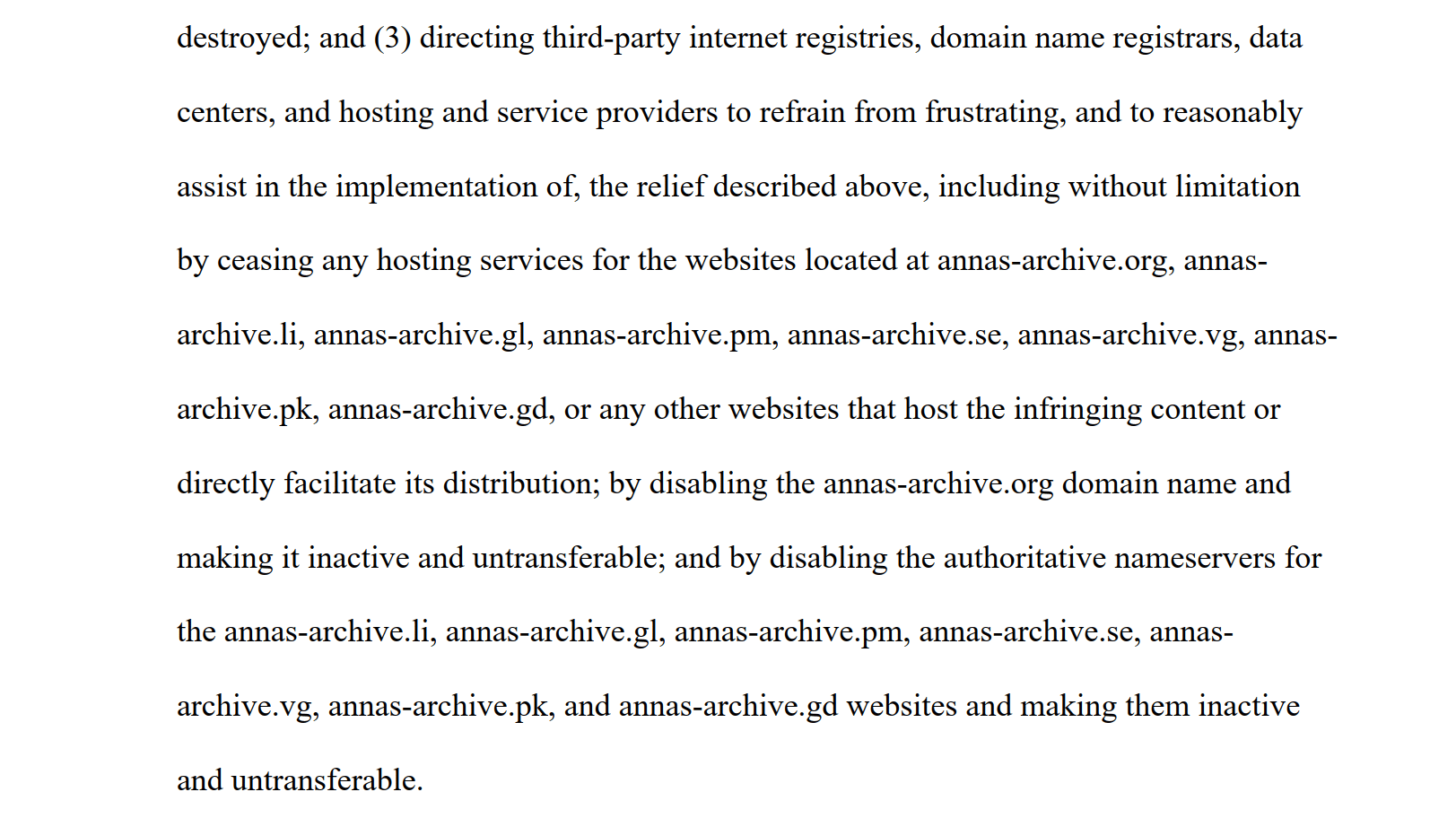
The publishers want to play their part in taking Anna’s Archive offline, and they therefore request an injunction to protect their copyrights. This proposed injunction requires the site and its operator to halt all infringing activity and destroy all pirated books and articles.
More importantly, the injunction would also require third-party intermediaries to stop providing services to the shadow library. This applies to data centers, and hosting and service providers, domain registrars, and domain registries.
The proposed injunction would apply to all current domain names, as well as “any other websites that host the infringing content or directly facilitate its distribution.”
At the time of writing, the court has yet to sign off on the requested injunction. Whether that order will be enough to keep Anna’s Archive offline for good, given its track record of quickly securing new domains, has yet to be seen.
—
A copy of the complaint, filed at the U.S. District Court for the Southern District of New York, is available here (pdf). The exhibit listing works in suit can be found here (pdf).
From: TF, for the latest news on copyright battles, piracy and more.
07:00 PM
Italian IPTV Pirates Pay €1,000 in Damages to Football League Serie A [TorrentFreak]
 Last May, the Guardia di Finanza announced that 2,282 pirate IPTV subscribers had been fined across 80 Italian provinces.
Last May, the Guardia di Finanza announced that 2,282 pirate IPTV subscribers had been fined across 80 Italian provinces.
The user details came from a criminal investigation in Lecce that dismantled a large IPTV operation, leaving behind a subscriber database that authorities put to immediate use.
Those fines, typically starting at €154 and rising to €5,000 for repeat offenders, were only the beginning. The same pirate IPTV (Pezzotto) users were in for more trouble.
Two Bills, Same Offense
In the autumn of 2025, DAZN sent letters to many of the pirate IPTV users who were already fined, offering to settle a civil damages claim for €500. This new payment request was in addition to the state fine, not instead of it.
Taking a page from this playbook, Serie A followed with its own damages demand. In January, the league’s CEO, Luigi De Siervo, announced that lawyers sent approximately 2,000 letters to individuals who were previously identified by the Guardia di Finanza, requesting €1,000 each as a settlement for the damages caused by their illegal streaming.
In late February, Serie A CEO Luigi De Siervo confirmed that the first payments have now been received. As with the DAZN case, these payments are also linked to Criminal Case no. 7719/2022 at the Tribunal of Lecce.
“Finally, even in our country, we are restoring the rule of law,” De Siervo said in a statement, adding that this is “only the beginning.”
“Those who use the pezzotto or illegally watch matches on apps, pirate IPTV, or via VPN, must know that they will be identified by the competent authorities, will have to pay fines of up to €5,000 as provided by law, and will above all be required to pay an additional €1,000 to Serie A as compensation for damages. Piracy is theft, period.”
Serie A does not mention how many payments it has received in response to the thousands of letters it sent out. This could be less than a handful, for now.
Follow The Money
It is clear that the messaging aims to deter future IPTV pirates, suggesting that even a VPN can’t secure them. While this statement is technically correct, it deserves some nuance.
The IPTV pirates who were identified in this case did not have their connections monitored in any way. Instead, the IPTV users were identified through their payment details, banking data, and other personal information obtained as part of a criminal investigation into an IPTV operator.
This is a notable distinction, as defense lawyers in the Lecce case have argued that some of the administrative fines issued lack technical evidence of actual piracy, resting solely on the payment trail.
One lawyer filed formal correction requests with Italian media, stressing that no IP addresses were identified, no devices were seized, and no specific copyrighted work was named in the citations. However, those challenges have not prevented the compensation letters from going out, or the payments from coming in.
Looming Threat
The Lecce case is one of several active proceedings. There are several other prosecutions, and, with permission from the Prosecutor’s Office, more details of pirate subscribers are reportedly shared with rightsholders.
Italy’s Minister for Sport, Andrea Abodi, went even further in October, suggesting that the names of those caught buying illegal subscriptions could eventually be published in a public naming and shaming campaign. “It’s beyond privacy concerns; it’s a crime,” he said at the time.
For now, however, the government appears content to let the financial pressure do the work. This also serves as a deterrent message, as those who received the €1,000 letter from Serie A but chose to ignore it potentially face a more expensive civil claim.
Meanwhile, the official Serie A website features a prominent advertisement for its long-running partner, 1XBET.
This is notable because the same gambling company the Motion Picture Association has flagged as a notorious piracy market, as it is frequently promoted through watermarked pirated movies and other advertisements on prominent pirate sites.
From: TF, for the latest news on copyright battles, piracy and more.
07:00 AM
Kanji of the Day: 善 [Kanji of the Day]
善
✍12
小6
virtuous, good, goodness
ゼン
よ.い い.い よ.く よし.とする
改善 (かいぜん) — betterment
最善 (さいぜん) — the very best
関係改善 (かんけいかいぜん) — improvement of relations
親善試合 (しんぜんじあい) — friendly match (game)
善意 (ぜんい) — virtuous mind
親善大使 (しんぜんたいし) — goodwill ambassador
善戦 (ぜんせん) — fighting a good fight
待遇改善 (たいぐうかいぜん) — improvement of labor conditions (labour)
善悪 (ぜんあく) — right and wrong
親善 (しんぜん) — friendship
Generated with kanjioftheday by Douglas Perkins.
Kanji of the Day: 没 [Kanji of the Day]
没
✍7
中学
drown, sink, hide, fall into, disappear, die
ボツ モツ
おぼ.れる しず.む ない
沈没 (ちんぼつ) — sinking
没頭 (ぼっとう) — immersing oneself in
水没 (すいぼつ) — submerge
埋没 (まいぼつ) — being buried
日没 (にちぼつ) — sunset
没後 (ぼつご) — after death
戦没者 (せんぼつしゃ) — persons who have fallen in battle
没する (ぼっする) — to sink
没収 (ぼっしゅう) — forfeiture
陥没 (かんぼつ) — cave-in
Generated with kanjioftheday by Douglas Perkins.
06:00 AM
Rethinking And Refreshing Techdirt’s Weekend Posts: We Want Your Feedback [Techdirt]
For many years now we’ve had two regular posts that come out on the weekends: our This Week In Techdirt History posts on Saturdays, and our Funniest/Most Insightful Comments Of The Week posts on Sundays. Sometimes we switch it up a little bit, replacing the history post with a special promotion or (as will be happening again soon!) with our Winner Spotlight posts for our annual public domain game jam.
This has been rolling along smoothly and we don’t plan any major changes, but we occasionally discuss whether there are tweaks we should make, and since I’m on vacation this week (and thus not around to write today’s comments post) we thought it would be a good time to check in with our readers and find out what you think.
In general, the weekend posts don’t get a lot of traffic, though that’s never been our reason for doing them anyway: they are for our community of commenters and long-time readers who we know appreciate them. Nevertheless, the relatively small audience for these posts is why we try not to expend too much time and effort creating them every week, as we’re all very busy around here and there are always a lot of projects on the go!
So with that in mind, we want to know: do folks like these posts? Is there stuff we can do to improve or refresh them going forward? Is there something else entirely you’d like to see as a weekly feature? Sound off in the comments, and we’ll be discussing the possibilities over the coming weeks.
There’s one change that we’ve already talked about and will likely be rolling out after the upcoming run of game jam winner spotlight posts: since Techdirt’s history has grown so long, and since frankly nobody wants to be repeatedly confronted with the fact that 2021 is already five years behind us, we’re going to ditch the “five years ago” section in the history round-ups and instead look at posts from ten, fifteen, and twenty years ago. Next year when we celebrate our 30th birthday, we might even change that up again to ten, twenty, and thirty year sections. Reaching further back just seems more fun and interesting than reminiscing on the recent past.
Also on the history posts, there’s a question I’d love some reader feedback on: is the “paragraph format” with a brief summary of some posts from the week worth keeping? Or would it be just as good (perhaps better) to go with just a bullet-list of selected headlines? Or something else?
As for the comments posts, these are our longest-running and most important tradition, as we’ve always valued our community of commenters and we want to highlight your contributions. However, as you know if you read them every week, lately it’s often been a struggle to populate the “funny” side of the list, and admittedly the quality of the Editor’s Choice selections can vary a lot, as it depends on how much time we (and especially I) have had to follow and engage in the comments on a given week.
So again we want your feedback: should anything change about the comment posts? Should we pivot away from Editor’s Choice and instead feature the top three winners-by-vote in each section (maybe retaining a single Editor’s Choice comment on each side, or just one for the week?) And how should we handle it when it’s a slow commenting week and there just aren’t enough highly-voted comments to make a post? (On especially slow weeks on the funny side, sometimes the “winners” are really just the chance recipients of a trickle of idle votes, and not really comments that make any sense to feature).
There’s also a similar question about the comments posts as there was about the history posts: is the brief written summary (in which I try to explain the context of a comment if and when it’s absolutely necessary to understand the comment itself) worthwhile? Or would a more dry bullet list that simply quotes and links to the winning comments and their authors suffice, leaving readers to go check out the full context as they wish?
Beyond these specific questions, we’re open to any and all thoughts on how the weekend posts should change (if they should change at all) and suggestions about anything else you might like to see. We’re not in a rush to make any changes, but it’s worth getting the conversation started. Let us know in the comments. (And if any suggestions are especially popular and get lots of votes, maybe they’ll turn up in next week’s winning comments post!)
02:00 AM
Confused about donations [Seth Godin's Blog on marketing, tribes and respect]
A suite at a New York Knicks game costs more than $30,000. Is that a donation to the team?
Why do we differentiate between the money spent on a Super Bowl ticket and the check we write for a worthy cause?
Does calling it a “donation” make it more valuable or less valuable to us?
Fundraisers can fall into the trap of believing that they’re asking for a favor or begging for a donation. But human beings, like all creatures, exchange time, money or risk in return for something. When that exchange is insufficient to cause action, we don’t do it.
The anonymous donor gets something. Something priceless, memorable and worthwhile: peace of mind.
The public donor, whether it’s the neighbor buying a raffle ticket for the scout fundraiser or the bigwig on the board of a museum, they get something as well. The status and connection they buy is a bargain, worth more than it costs. In fact, if it wasn’t worth more than it costs, they wouldn’t buy it.
The fundraiser isn’t asking for a favor. They’re offering an opportunity.
01:00 AM
Wikimedia Commons picture of the day for March 1 [Wikimedia Commons picture of the day feed]
| Picture of the day |
|---|

|
Famous sanctuary of the temple of Ramses II, Abu Simbel, Egypt. The Great Temple at Abu Simbel, which took about twenty years to build, was completed around year 24 of the reign of Ramesses the Great (which corresponds to 1265 BC). It was dedicated to the gods Amun, Ra-Horakhty, and Ptah, as well as to the deified Ramesses himself. It is generally considered the grandest and most beautiful of the temples commissioned during the reign of Ramesses II, and one of the most beautiful in Egypt. In the sanctuary are rock cut sculptures of four seated figures: Ra-Horakhty, the deified king Ramesses, and the gods Amun Ra and Ptah, the main divinities in that period. It is believed that the axis of the temple was positioned by the ancient Egyptian architects in such a way that on October 22 and February 22 (allegedly the king's birthday and coronation day, respectively), the rays of the sun would penetrate the sanctuary and illuminate the sculptures on the back wall, except for the statue of Ptah, a god connected with the realm of the dead, who always remained in the dark. People gather at Abu Simbel on these days to witness this.
|
Wikimedia Commons picture of the day for March 2 [Wikimedia Commons picture of the day feed]
| Picture of the day |
|---|

|
The historic Geigersberg vineyard, northeast of the Sachsenheim district of Ochsenbach in Germany, still retains many of its old dry stone walls and is home to rare plant and animal species.
|
Wikimedia Commons picture of the day for March 3 [Wikimedia Commons picture of the day feed]
| Picture of the day |
|---|

|
Doll (musha-ningyo) featuring Takenouchi no Sukune, minister of Emperor Ōjin; end of the Edo period, 19th century, Japan. Ann and Gabriel Barbier-Mueller Museum, Dallas (Texas) ; the photograph was taken during an exhibition in the Musée des Arts Premiers in Paris
|
Wikimedia Commons picture of the day for March 4 [Wikimedia Commons picture of the day feed]
Wikimedia Commons picture of the day for March 5 [Wikimedia Commons picture of the day feed]
| Picture of the day |
|---|

|
Ground shoot of one Euphorbia griffithii Beautifully colored ground shoot emerges in a natural border. Focus stack of 15 photos.
|
Wikimedia Commons picture of the day for March 6 [Wikimedia Commons picture of the day feed]
| Picture of the day |
|---|

|
Two Glanville fritillaries (Melitaea cinxia) on a red clover. Today is Kaede Hondo's birthday, she voiced Kokoro Yotsuba in Kamisama Minarai: Himitsu no Cocotama.
|
Wikimedia Commons picture of the day for March 7 [Wikimedia Commons picture of the day feed]
| Picture of the day |
|---|

|
A California Sheephead at Ensenada´s fishmarket (Mercado Negro), Baja California, México. The California Sheephead (Semicossyphus pulcher) is characterized by its wrasse-like shape, and three different color patterns for juveniles, adult males, and adult females.
|
Wikimedia Commons picture of the day for March 8 [Wikimedia Commons picture of the day feed]
| Picture of the day |
|---|

|
Tower Clock manufacturer in Morez, France - Louis-Delphin Odobey Cadet. Daylight saving time begins today in much of the Western Hemisphere.
|
Sunday 2026-03-08
02:00 PM
Pluralistic: The web is bearable with RSS (07 Mar 2026) [Pluralistic: Daily links from Cory Doctorow]
->->->->->->->->->->->->->->->->->->->->->->->->->->->->->
Top Sources:
None
-->

Today's links
- The web is bearable with RSS: And don't forget "Reader Mode."
- Hey look at this: Delights to delectate.
- Object permanence: Eyemodule x Disneyland; Scott Walker lies; Brother's demon-haunted printer; 4th Amendment luggage tape; Sanders x small donors v media; US police killings tallied.
- Upcoming appearances: Where to find me.
- Recent appearances: Where I've been.
- Latest books: You keep readin' em, I'll keep writin' 'em.
- Upcoming books: Like I said, I'll keep writin' 'em.
- Colophon: All the rest.
The web is bearable with RSS (permalink)
Never let them tell you that enshittification was a mystery. Enshittification isn't downstream of the "iron laws of economics" or an unrealistic demand by "consumers" to get stuff for free.
Enshittification comes from specific policy choices, made by named individuals, that had the foreseeable and foreseen result of making the web worse:
https://pluralistic.net/2025/10/07/take-it-easy/#but-take-it
Like, there was once a time when an ever-increasing proportion of web users kept tabs on what was going on with RSS. RSS is a simple, powerful way for websites to publish "feeds" of their articles, and for readers to subscribe to those feeds and get notified when something new was posted, and even read that new material right there in your RSS reader tab or app.
RSS is simple and versatile. It's the backbone of podcasts (though Apple and Spotify have done their best to kill it, along with public broadcasters like the BBC, all of whom want you to switch to proprietary apps that spy on you and control you). It's how many automated processes communicate with one another, untouched by human hands. But above all, it's a way to find out when something new has been published on the web.
RSS's liftoff was driven by Google, who released a great RSS reader called "Google Reader" in 2007. Reader was free and reliable, and other RSS readers struggled to compete with it, with the effect that most of us just ended up using Google's product, which made it even harder to launch a competitor.
But in 2013, Google quietly knifed Reader. I've always found the timing suspicious: it came right in the middle of Google's desperate scramble to become Facebook, by means of a product called Google Plus (G+). Famously, Google product managers' bonuses depended on how much G+ engagement they drove, with the effect that every Google product suddenly sprouted G+ buttons that either did something stupid, or something that confusingly duplicated existing functionality (like commenting on Youtube videos).
Google treated G+ as an existential priority, and for good reason. Google was running out of growth potential, having comprehensively conquered Search, and having repeatedly demonstrated that Search was a one-off success, with nearly every other made-in-Google product dying off. What successes Google could claim were far more modest, like Gmail, Google's Hotmail clone. Google augmented its growth by buying other peoples' companies (Blogger, YouTube, Maps, ad-tech, Docs, Android, etc), but its internal initiatives were turkeys.
Eventually, Wall Street was going to conclude that Google had reached the end of its growth period, and Google's shares would fall to a fraction of their value, with a price-to-earnings ratio commensurate with a "mature" company.
Google needed a new growth story, and "Google will conquer Facebook's market" was a pretty good one. After all, investors didn't have to speculate about whether Facebook was profitable, they could just look at Facebook's income statements, which Google proposed to transfer to its own balance sheet. The G+ full-court press was as much a narrative strategy as a business strategy: by tying product managers' bonuses to a metric that demonstrated G+'s rise, Google could convince Wall Street that they had a lot of growth on their horizon.
Of course, tying individual executives' bonuses to making a number go up has a predictably perverse outcome. As Goodhart's law has it, "Any metric becomes a target, and then ceases to be a useful metric." As soon as key decision-makers' personal net worth depending on making the G+ number go up, they crammed G+ everywhere and started to sneak in ways to trigger unintentional G+ sessions. This still happens today – think of how often you accidentally invoke an unbanishable AI feature while using Google's products (and products from rival giant, moribund companies relying on an AI narrative to convince investors that they will continue to grow):
https://pluralistic.net/2025/05/02/kpis-off/#principal-agentic-ai-problem
Like I said, Google Reader died at the peak of Google's scramble to make the G+ number go up. I have a sneaking suspicion that someone at Google realized that Reader's core functionality (helping users discover, share and discuss interesting new web pages) was exactly the kind of thing Google wanted us to use G+ for, and so they killed Reader in a bid to drive us to the stalled-out service they'd bet the company on.
If Google killed Reader in a bid to push users to discover and consume web pages using a proprietary social media service, they succeeded. Unfortunately, the social media service they pushed users into was Facebook – and G+ died shortly thereafter.
For more than a decade, RSS has lain dormant. Many, many websites still emit RSS feeds. It's a default behavior for WordPress sites, for Ghost and Substack sites, for Tumblr and Medium, for Bluesky and Mastodon. You can follow edits to Wikipedia pages by RSS, and also updates to parcels that have been shipped to you through major couriers. Web builders like Jason Kottke continue to surface RSS feeds for elaborate, delightful blogrolls:
There are many good RSS readers. I've been paying for Newsblur since 2011, and consider the $36 I send them every year to be a very good investment:
But RSS continues to be a power user-coded niche, despite the fact that RSS readers are really easy to set up and – crucially – make using the web much easier. Last week, Caroline Crampton (co-editor of The Browser) wrote about her experiences using RSS:
https://www.carolinecrampton.com/the-view-from-rss/
As Crampton points out, much of the web (including some of the cruftiest, most enshittified websites) publish full-text RSS feeds, meaning that you can read their articles right there in your RSS reader, with no ads, no popups, no nag-screens asking you to sign up for a newsletter, verify your age, or submit to their terms of service.
It's almost impossible to overstate how superior RSS is to the median web page. Imagine if the newsletters you followed were rendered with black, clear type on a plain white background (rather than the sadistically infinitesimal, greyed-out type that designers favor thanks to the unkillable urban legend that black type on a white screen causes eye-strain). Imagine reading the web without popups, without ads, without nag screens. Imagine reading the web without interruptors or "keep reading" links.
Now, not every website publishes a fulltext feed. Often, you will just get a teaser, and if you want to read the whole article, you have to click through. I have a few tips for making other websites – even ones like Wired and The Intercept – as easy to read as an RSS reader, at least for Firefox users.
Firefox has a built-in "Reader View" that re-renders the contents of a web-page as black type on a white background. Firefox does some kind of mysterious calculation to determine whether a page can be displayed in Reader View, but you can override this with the Activate Reader View, which adds a Reader View toggle for every page:
https://addons.mozilla.org/en-US/firefox/addon/activate-reader-view/
Lots of websites (like The Guardian) want you to login before you can read them, and even if you pay to subscribe to them, these sites often want you to re-login every time you visit them (especially if you're running a full suite of privacy blockers). You can skip this whole process by simply toggling Reader View as soon as you get the login pop up. On some websites (like The Verge and Wired), you'll only see the first couple paragraphs of the article in Reader View. But if you then hit reload, the whole article loads.
Activate Reader View puts a Reader View toggle on every page, but clicking that toggle sometimes throws up an error message, when the page is so cursed that Firefox can't figure out what part of it is the article. When this happens, you're stuck reading the page in the site's own default (and usually terrible) view. As you scroll down the page, you will often hit pop-ups that try to get you to sign up for a mailing list, agree to terms of service, or do something else you don't want to do. Rather than hunting for the button to close these pop-ups (or agree to objectionable terms of service), you can install "Kill Sticky," a bookmarklet that reaches into the page's layout files and deletes any element that isn't designed to scroll with the rest of the text:
https://github.com/t-mart/kill-sticky
Other websites (like Slashdot and Core77) load computer-destroying Javascript (often as part of an anti-adblock strategy). For these, I use the "Javascript Toggle On and Off" plugin, which lets you create a blacklist of websites that aren't allowed to run any scripts:
https://addons.mozilla.org/en-US/firefox/addon/javascript-toggler/
Some websites (like Yahoo) load so much crap that they defeat all of these countermeasures. For these websites, I use the "Element Blocker" plug-in, which lets you delete parts of the web-page, either for a single session, or permanently:
https://addons.mozilla.org/en-US/firefox/addon/element-blocker/
It's ridiculous that websites put so many barriers up to a pleasant reading experience. A slow-moving avalanche of enshittogenic phenomena got us here. There's corporate enshittification, like Google/Meta's monopolization of ads and Meta/Twitter's crushing of the open web. There's regulatory enshittification, like the EU's failure crack down on companies the pretend that forcing you to click an endless stream of "cookie consent" popups is the same as complying with the GDPR.
Those are real problems, but they don't have to be your problem, at least when you want to read the web. A couple years ago, I wrote a guide to using RSS to improve your web experience, evade lock-in and duck algorithmic recommendation systems:
Customizing your browser takes this to the next level, disenshittifying many websites – even if they block or restrict RSS. Most of this stuff only applies to desktop browsers, though. Mobile browsers are far more locked down (even mobile Firefox – remember, every iOS browser, including Firefox, is just a re-skinned version of Safari, thanks to Apple's ban rival browser engines). And of course, apps are the worst. An app is just a website skinned in the right kind of IP to make it a crime to improve it in any way:
https://pluralistic.net/2024/05/07/treacherous-computing/#rewilding-the-internet
And even if you do customize your mobile browser (Android Firefox lets you do some of this stuff), many apps (Twitter, Tumblr) open external links in their own browser (usually an in-app Chrome instance) with all the bullshit that entails.
The promise of locked-down mobile platforms was that they were going to "just work," without any of the confusing customization options of desktop OSes. It turns out that taking away those confusing customization options was an invitation to every enshittifier to turn the web into an unreadable, extractive, nagging mess. This was the foreseeable – and foreseen – consequence of a new kind of technology where everything that isn't mandatory is prohibited:
https://memex.craphound.com/2010/04/01/why-i-wont-buy-an-ipad-and-think-you-shouldnt-either/
Hey look at this (permalink)

- The Real Litmus Test for Democratic Presidential Candidates https://www.hamiltonnolan.com/p/the-real-litmus-test-for-democratic
-
Users fume over Outlook.com email 'carnage' https://www.theregister.com/2026/03/04/users_fume_at_outlookcom_email/
-
You Bought Zuck’s Ray-Bans. Now Someone in Nairobi Is Watching You Poop. https://blog.adafruit.com/2026/03/04/you-bought-zucks-ray-bans-now-someone-in-nairobi-is-watching-you-poop/
-
Indefinite Book Club Hiatus https://whatever.scalzi.com/2026/03/03/indefinite-book-club-hiatus/
-
Art Bits from HyperCard https://archives.somnolescent.net/web/mari_v2/junk/hypercard/
Object permanence (permalink)
#25yrsago 200 Eyemodule photos from Disneyland https://craphound.com/030401/
#20yrsago Fourth Amendment luggage tape https://ideas.4brad.com/node/367
#15yrsago Glenn Beck’s syndicator runs a astroturf-on-demand call-in service for radio programs https://web.archive.org/web/20110216081007/http://www.tabletmag.com/life-and-religion/58759/radio-daze/
#15yrsago 20 lies from Scott Walker https://web.archive.org/web/20110308062319/https://filterednews.wordpress.com/2011/03/05/20-lies-and-counting-told-by-gov-walker/
#10yrsago The correlates of Trumpism: early mortality, lack of education, unemployment, offshored jobs https://web.archive.org/web/20160415000000*/https://www.washingtonpost.com/news/wonk/wp/2016/03/04/death-predicts-whether-people-vote-for-donald-trump/
#10yrsago Hacking a phone’s fingerprint sensor in 15 mins with $500 worth of inkjet printer and conductive ink https://web.archive.org/web/20160306194138/http://www.cse.msu.edu/rgroups/biometrics/Publications/Fingerprint/CaoJain_HackingMobilePhonesUsing2DPrintedFingerprint_MSU-CSE-16-2.pdf
#10yrsago Despite media consensus, Bernie Sanders is raising more money, from more people, than any candidate, ever https://web.archive.org/web/20160306110848/https://www.washingtonpost.com/politics/sanders-keeps-raising-money–and-spending-it-a-potential-problem-for-clinton/2016/03/05/a8d6d43c-e2eb-11e5-8d98-4b3d9215ade1_story.html
#10yrsago Calculating US police killings using methodologies from war-crimes trials https://granta.com/violence-in-blue/
#1yrago Brother makes a demon-haunted printer https://pluralistic.net/2025/03/05/printers-devil/#show-me-the-incentives-i-will-show-you-the-outcome
#1yrago Two weak spots in Big Tech economics https://pluralistic.net/2025/03/06/privacy-last/#exceptionally-american
Upcoming appearances (permalink)

- San Francisco: Launch for Cindy Cohn's "Privacy's Defender" (City Lights), Mar 10
https://citylights.com/events/cindy-cohn-launch-party-for-privacys-defender/ -
Barcelona: Enshittification with Simona Levi/Xnet (Llibreria Finestres), Mar 20
https://www.llibreriafinestres.com/evento/cory-doctorow/ -
Berkeley: Bioneers keynote, Mar 27
https://conference.bioneers.org/ -
Montreal: Bronfman Lecture (McGill) Apr 10
https://www.eventbrite.ca/e/artificial-intelligence-the-ultimate-disrupter-tickets-1982706623885 -
London: Resisting Big Tech Empires (LSBU)
https://www.tickettailor.com/events/globaljusticenow/2042691 -
Berlin: Re:publica, May 18-20
https://re-publica.com/de/news/rp26-sprecher-cory-doctorow -
Berlin: Enshittification at Otherland Books, May 19
https://www.otherland-berlin.de/de/event-details/cory-doctorow.html -
Hay-on-Wye: HowTheLightGetsIn, May 22-25
https://howthelightgetsin.org/festivals/hay/big-ideas-2
Recent appearances (permalink)
- The Virtual Jewel Box (U Utah)
https://tanner.utah.edu/podcast/enshittification-cory-doctorow-matthew-potolsky/ -
Tanner Humanities Lecture (U Utah)
https://www.youtube.com/watch?v=i6Yf1nSyekI -
The Lost Cause
https://streets.mn/2026/03/02/book-club-the-lost-cause/ -
Should Democrats Make A Nuremberg Caucus? (Make It Make Sense)
https://www.youtube.com/watch?v=MWxKrnNfrlo -
Making The Internet Suck Less (Thinking With Mitch Joel)
https://www.sixpixels.com/podcast/archives/making-the-internet-suck-less-with-cory-doctorow-twmj-1024/
Latest books (permalink)
- "Canny Valley": A limited edition collection of the collages I create for Pluralistic, self-published, September 2025 https://pluralistic.net/2025/09/04/illustrious/#chairman-bruce
-
"Enshittification: Why Everything Suddenly Got Worse and What to Do About It," Farrar, Straus, Giroux, October 7 2025
https://us.macmillan.com/books/9780374619329/enshittification/ -
"Picks and Shovels": a sequel to "Red Team Blues," about the heroic era of the PC, Tor Books (US), Head of Zeus (UK), February 2025 (https://us.macmillan.com/books/9781250865908/picksandshovels).
-
"The Bezzle": a sequel to "Red Team Blues," about prison-tech and other grifts, Tor Books (US), Head of Zeus (UK), February 2024 (thebezzle.org).
-
"The Lost Cause:" a solarpunk novel of hope in the climate emergency, Tor Books (US), Head of Zeus (UK), November 2023 (http://lost-cause.org).
-
"The Internet Con": A nonfiction book about interoperability and Big Tech (Verso) September 2023 (http://seizethemeansofcomputation.org). Signed copies at Book Soup (https://www.booksoup.com/book/9781804291245).
-
"Red Team Blues": "A grabby, compulsive thriller that will leave you knowing more about how the world works than you did before." Tor Books http://redteamblues.com.
-
"Chokepoint Capitalism: How to Beat Big Tech, Tame Big Content, and Get Artists Paid, with Rebecca Giblin", on how to unrig the markets for creative labor, Beacon Press/Scribe 2022 https://chokepointcapitalism.com
Upcoming books (permalink)
- "The Reverse-Centaur's Guide to AI," a short book about being a better AI critic, Farrar, Straus and Giroux, June 2026
-
"Enshittification, Why Everything Suddenly Got Worse and What to Do About It" (the graphic novel), Firstsecond, 2026
-
"The Post-American Internet," a geopolitical sequel of sorts to Enshittification, Farrar, Straus and Giroux, 2027
-
"Unauthorized Bread": a middle-grades graphic novel adapted from my novella about refugees, toasters and DRM, FirstSecond, 2027
-
"The Memex Method," Farrar, Straus, Giroux, 2027
Colophon (permalink)
Today's top sources:
Currently writing: "The Post-American Internet," a sequel to "Enshittification," about the better world the rest of us get to have now that Trump has torched America (1012 words today, 45361 total)
- "The Reverse Centaur's Guide to AI," a short book for Farrar, Straus and Giroux about being an effective AI critic. LEGAL REVIEW AND COPYEDIT COMPLETE.
-
"The Post-American Internet," a short book about internet policy in the age of Trumpism. PLANNING.
-
A Little Brother short story about DIY insulin PLANNING

This work – excluding any serialized fiction – is licensed under a Creative Commons Attribution 4.0 license. That means you can use it any way you like, including commercially, provided that you attribute it to me, Cory Doctorow, and include a link to pluralistic.net.
https://creativecommons.org/licenses/by/4.0/
Quotations and images are not included in this license; they are included either under a limitation or exception to copyright, or on the basis of a separate license. Please exercise caution.
How to get Pluralistic:
Blog (no ads, tracking, or data-collection):
Newsletter (no ads, tracking, or data-collection):
https://pluralistic.net/plura-list
Mastodon (no ads, tracking, or data-collection):
Bluesky (no ads, possible tracking and data-collection):
https://bsky.app/profile/doctorow.pluralistic.net
Medium (no ads, paywalled):
https://doctorow.medium.com/
https://twitter.com/doctorow
Tumblr (mass-scale, unrestricted, third-party surveillance and advertising):
https://mostlysignssomeportents.tumblr.com/tagged/pluralistic
"When life gives you SARS, you make sarsaparilla" -Joey "Accordion Guy" DeVilla
READ CAREFULLY: By reading this, you agree, on behalf of your employer, to release me from all obligations and waivers arising from any and all NON-NEGOTIATED agreements, licenses, terms-of-service, shrinkwrap, clickwrap, browsewrap, confidentiality, non-disclosure, non-compete and acceptable use policies ("BOGUS AGREEMENTS") that I have entered into with your employer, its partners, licensors, agents and assigns, in perpetuity, without prejudice to my ongoing rights and privileges. You further represent that you have the authority to release me from any BOGUS AGREEMENTS on behalf of your employer.
ISSN: 3066-764X
Just for Skeets and Giggles (3.7.26) [The Status Kuo]
My editor is out today, so please excuse all typos and autocorrect errors. They are my worst enemas!
This week was enough for all of us to want to escape this world.
We’re all, distressingly, many steps closer to the end.
“Relatively” speaking, evil abounds.
Trump’s not-a-war upon Iran was of course top of many minds, including Jimmy Fallon’s, who managed to capture the absurdity of the horrifying moment we’re now in.
Here’s another view into that head.
Saturday Night Live managed to swap this in for its cold open last weekend.
This is seriously a valid question now.
You laugh, but this might actually work with the MAGA holdouts.
Stephen Colbert weighed in, discussing the last Middle East war, the current Middle East war, and our ex post facto “rubber” stamp Congress.
The writers of Shrek predicted something like this long ago.
Surely the rich will send their own children into battle, too, right? Or nah.
Trump was in Mar-a-Lago, not the White House Situation Room, when we started dropping bombs.
Placement is everything.
One of the first things that happened? Our allies in Kuwait shot down three of our fighter jets, or basically all the money DOGE ever “saved” through cuts.
I’d say barely so here:
Speaking of dead things,
Hearing Jon Stewart sound off is a balm for what remains of our national soul, which the wart hog in the Oval Office soils daily.
The international humor these days is also quite dark.
It’s disturbing that reasonable minds must now give this theory some consideration:
NYTPitchbot is pitch perfect.
This would be a crime against humanity, but otherwise I agree.
If you’ve been following the Anthropic / OpenAI wars, this hits hard.
If you need a refresher…
May have to borrow this zinger going forward.
The right circulated this video widely without listening to or understanding the lyrics, just like how they love “Born in the USA.”
After one week, the war has expanded and now engulfs the region, and our Western allies may get pulled in as they seek to defend bases from missile fire. It’s already producing some historic parallels.
On the subject of history, here it is on repeat.
Nothing like a hands-on government.
Slow. Clap.
Why not go worldwide, right?
We should call it “Epic Furry” from now on.
This running joke only gets better over time.
Speaking of Marco,
Sometimes puppetry is the best way to convey what’s going on.
The justification for the war keeps changing. Trump recently went with Armageddon.
On the subject of horrible people,
Turns out, they killed the dad but the son-in-waiting survived.
If there is any silver lining to this horrifying violence, it is that the MAGA America First crowd has started to walk away in significant numbers. Those still left, however…
Candace Owen somehow made this war about (checks notes) Charlie Kirk.
The cultists treat Trump like he’s Jesus. But what if…
This took the best kind of turn.
Also, yes. Let’s keep the attention where it belongs.
In non-war news, Kristi Noem appeared before Congress to testify. BIG mistake.
Her testimony was so disastrous that even Trump cut her loose, probably because she said (as she’s said before, by the way) that Trump himself approved $200 million in ads to promote her personal brand.
Trump reassigned her to a new made-up position, and the Late Night comedians had a field day.
Well played, sir.
Okay, this image could be AI, but there were in fact barks of joy heard round the nation.
Gavin Newsom with the one year in memoriam. Damn his team is fast!
Tweet of the day:
Rep. Moskowitz with the end zone spike.
For the Veep fans out there…
Cricket GOT some justice.
Sure, but don’t say “ice’ around her now.
Trump wants to put Markwayne Mullin in the job. Can we talk about who names their kid that?
Can’t stop laughing!
Racial minorities have pretty much had it with the MAGA white crowd.
The right keeps trying to wage the culture war even while an actual war rages. It’s going poorly.
This is a pledge break! That means you get a chance to say thanks with a paid subscription to The Status Kuo. Your support helps make it possible to keep this newsletter free for those on fixed income or disability.
Let’s start this section off with a couple of kitties! Check out the clean execution by this fella. Hockey goalie in the making!
I don’t know what I’d name him, but I’d never stop taking his picture.
My corgi DEFINITELY judges me.
Wait for the zoom in.
Location, location, location.
Rockstar is back with his signature voiceover, with an assist from a friend!
Wish Casper a Happy Birthday!
I would have the same reaction, TBH.
This one really made an ass out of himself.
This one is for all of us.
Story sent me cackling.
We need experts to weigh in.
Go glad to see this angel is soaring.
Time for a doggo dad joke!
Okay just one more, from the mouths of our alien overlords who apparently love dad jokes as much as I do.
Have a great weekend!
Jay
06:00 AM
This Week In Techdirt History: March 1st – 7th [Techdirt]
Five Years Ago
This week in 2021, while AT&T was apparently committed to being comically hypocritical about Section 230, Utah was prematurely trying to dance on 230’s grave with a new and extremely horrible “free speech” bill that was a disaster in the making, and we had Ron Wyden and Chris Cox on the Techdirt Podcast to talk about why 230 matters so much. Washington State was also spitting on Section 230 by going after Google for political ads, while Arizona was moving forward with a law that would force Google and Apple to open up payments in app stores. Meanwhile, Parler dropped one lawsuit against Amazon then filed an equally dumb new one, a reporter sued the DOJ to find out if it was helping Devin Nunes try to unmask the @DevinCow Twitter account, and the FBI director was using January 6th to once again ask for encryption backdoors.
Ten Years Ago
This week in 2016, it was the CIA and NSA directors talking about encryption, specifically blaming the media for terrorists using it. Congress actually seemed pretty angry about the FBI’s belief that the courts could force Apple to help it get into iPhones, and we read all 20 court filings in support of Apple in the fight, as well as the rather problematic filings from law enforcement groups on the side of the FBI, though nothing was as insane as the brief from the San Bernardino District Attorney. Meanwhile, Brazil arrested a Facebook executive because the company refused to reveal info on WhatsApp users, but a different judge quickly ordered his release. And, in a post that seems almost quaint in its obviousness now, we wrote about how Donald Trump could definitely cause problems for free speech and the First Amendment.
Fifteen Years Ago
This week in 2011, ICE’s boss was insisting it was okay to ignore the constitution and seize domain names to help companies, Senator Al Franken was defending censoring the internet for the sake of Hollywood’s business model, and Rep. Darrell Issa was insisting that the IP Czar should be able to pin liability for file sharing on third parties (not unlike what Rosetta Stone was demanding while writing in support of COICA). Meanwhile, UK publishers were speaking out against fair use, the BSA was fearmongering about open standards, and new proposed legislation to protect the IP of farmers would make it a felony to photograph farms.
Kanji of the Day: 欠 [Kanji of the Day]
欠
✍4
小4
lack, gap, fail, yawning radical (no. 76)
ケツ ケン
か.ける か.く
不可欠 (ふかけつ) — indispensable
欠席 (けっせき) — absence
欠点 (けってん) — fault
欠け (かけ) — fragment
欠場 (けつじょう) — absence
欠ける (かける) — to chip
欠陥 (けっかん) — defect
補欠 (ほけつ) — filling a vacancy
欠く (かく) — to chip
欠如 (けつじょ) — lack
Generated with kanjioftheday by Douglas Perkins.
Kanji of the Day: 描 [Kanji of the Day]
描
✍11
中学
sketch, compose, write, draw, paint
ビョウ
えが.く か.く
描く (えがく) — to draw
描写 (びょうしゃ) — depiction
絵を描く (えをえがく) — to paint (draw) a picture
点描 (てんびょう) — sketching
手描き (てがき) — handwriting
描き出す (えがきだす) — to delineate
思い描く (おもいえがく) — to imagine
絵描き (えかき) — painter
描画 (びょうが) — drawing
心理描写 (しんりびょうしゃ) — psychological description
Generated with kanjioftheday by Douglas Perkins.
01:00 AM
If they knew… [Seth Godin's Blog on marketing, tribes and respect]
Some organizations and marketers thrive on the uninformed consumer. They seek out people who don’t know, and who aren’t particularly good at decision making.
Others do their best work when the customer knows what’s up and is making an informed choice.
Are you closing the sale or opening it?
If your prospects knew everything you know, would they choose you?
When marketers sign up for the iterative process of education and sophistication, our path is clear.
And if we sign up to confuse and manipulate, that path is clear as well.